T-Mobile suffers another system breach, this time at the hands of teen hackers

Cyber-crime gang Lapsus$ which had successfully hacked NVIDIA, Samsung, and Microsoft, was able to get into T-Mobile's systems multiple times in March, per Krebs on Security.
LAPSUS$ was run by a bunch of teenagers apparently and its most active members are now behind the bars. Krebs on Security obtained a week's worth of private chats between key LAPSUS$ members, which gives a glimpse into their modus operandi.
LAPSUS$ was obsessed with obtaining source code from tech companies. The gang used to gain initial access to its targets by buying credentials from sites like Russian Market. The trickier part was gaining access to internal company tools.
They relentlessly targeted T-Mobile employees and were able to breach the carrier's system multiple times last month, giving them access to source code for a range of projects. The rogue group briefly considered SIM swaps, which would have let them hijack someone else's number, which could have allowed them to conduct activities like password resets.
LAPSUS$ gained access to the internal customer accounts management tool Atlas on March 19 and explored high-profile T-Mobile accounts associated with the FBI and Department of Defense. They weren't able to go any further than that because those accounts required additional verifications before any changes could be made.
The group leader, who is believed to be a 17-year-old from the U.K. and is referred to by nicknames "White," "WhiteDoxbin," and "Oklaqq," eventually terminated the VPN connection that let them access T-Mobile’s network. He then proceeded to gain access to the carrier's Slack and Bitbucket accounts.
He was also able to download over 30,000 source code repositories from T-Mobile. It looks like this is when their access was revoked, as, in the words of White, "Cloning 30k repos four times in 24 hours isn’t very normal."
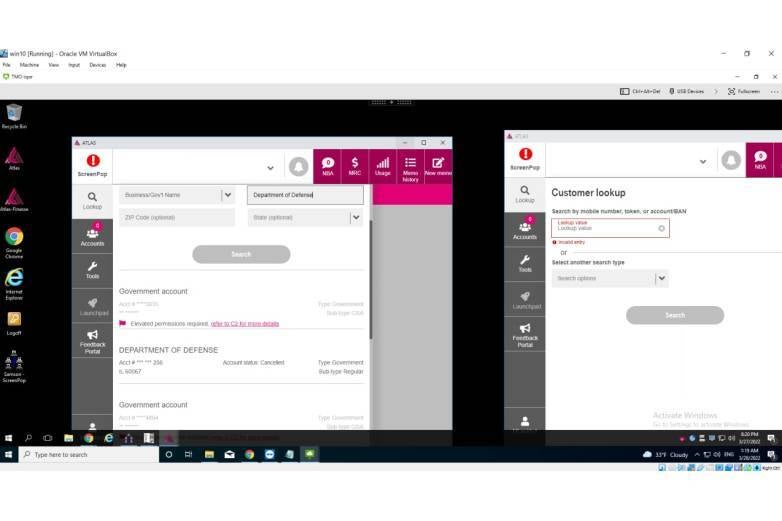
LAPSUS$ may had intended to target high-profile T-Mobile accounts
T-Mobile has confirmed the attacks but has assured that the hackers weren't able to steal any customer or government information.
Several weeks ago, our monitoring tools detected a bad actor using stolen credentials to access internal systems that house operational tools software. The systems accessed contained no customer or government information or other similarly sensitive information, and we have no evidence that the intruder was able to obtain anything of value. Our systems and processes worked as designed, the intrusion was rapidly shut down and closed off, and the compromised credentials used were rendered obsolete.
This is the seventh data breach T-Mobile has confirmed since 2018. A few days back, the carrier warned customers about unblockable phishing attacks.










Things that are NOT allowed: