Signal wants to be quantum-proof, as quantum computers in 5-10 years will be able to crack encryptions
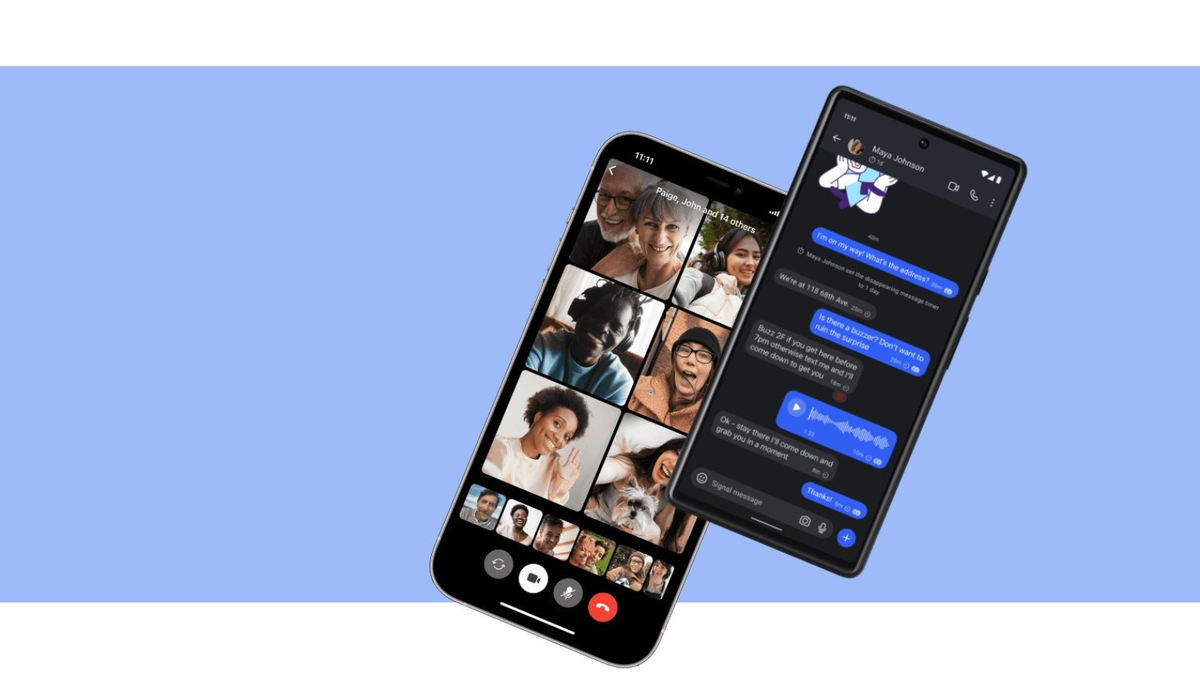
It doesn’t matter where you position yourself on the paranoid spectrum, encrypted messaging is getting more and more popular. And in the world of enciphered chatting, Signal has a special place. Now the popular app wants to get even more secure by shielding itself from an alleged threat that’s to come 5 to 10 years from now.
That’s where things are starting to get quantum. Signal is upgrading its cyber security precautions by creating a new specification called PQXDH. We’ll get into it – to a certain degree because we lack the academic degree – but for now, its purpose is to protect against future quantum computers that could break encryption (via Android Police).
“With this upgrade, we are adding a layer of protection against the threat of a quantum computer being built in the future that is powerful enough to break current encryption standards”, reads the Signal blog post that announces the PQXDH.
The aforementioned excellent Signal blog post explains how future quantum computers could pose a threat to current standard encrypted messaging. First of all, quantum computers are not better or worse than “regular” computers – they are a completely different kind of beast. Instead of bits as in a classical computer, quantum computers operate on qubits. Rather than 0 or 1, qubits can exist in a superposition of states, in some sense allowing them to be both values at once.
Quantum computing will probably not find its way to our homes (although Microsoft Quantum or MacQ sounds cool for OS naming), but they’ll likely be built to aid us in the tasks we give supercomputers to tackle today: modeling protein folding, forecasting weather, or factoring large numbers.
“Although quantum computers already exist, the systems known to exist today do not yet have enough qubits to pose a threat to the public-key cryptography that Signal currently uses. However, if a sufficiently powerful quantum computer were built in the future, it could be used to compute a private key from a public key thereby breaking encrypted messages”, the Signal team warns.
They say there are many timeline predictions for when a sufficiently powerful quantum computer may be created. Some say it’s only a couple of years from now, others say it can’t be properly done for the next 30 or more years. The middle ground seems to be around the 5 to 10-year time horizon. “We are not in a position to judge which timeline is most likely, but we do see a real and growing risk which means we need to take steps today to address the future possibility of a large enough quantum computer being created”, they say.
The official specification page for Signal’s PQXDH has mercy on us and starts gently: PQXDH stands for Post-Quantum Extended Diffie-Hellman key agreement protocol. PQXDH establishes a shared secret key between two parties who mutually authenticate each other based on public keys. PQXDH provides post-quantum forward secrecy and a form of cryptographic deniability but still relies on the hardness of the discrete log problem for mutual authentication in this revision of the protocol.
Why be afraid?
The aforementioned excellent Signal blog post explains how future quantum computers could pose a threat to current standard encrypted messaging. First of all, quantum computers are not better or worse than “regular” computers – they are a completely different kind of beast. Instead of bits as in a classical computer, quantum computers operate on qubits. Rather than 0 or 1, qubits can exist in a superposition of states, in some sense allowing them to be both values at once.
Quantum computing will probably not find its way to our homes (although Microsoft Quantum or MacQ sounds cool for OS naming), but they’ll likely be built to aid us in the tasks we give supercomputers to tackle today: modeling protein folding, forecasting weather, or factoring large numbers.
They say there are many timeline predictions for when a sufficiently powerful quantum computer may be created. Some say it’s only a couple of years from now, others say it can’t be properly done for the next 30 or more years. The middle ground seems to be around the 5 to 10-year time horizon. “We are not in a position to judge which timeline is most likely, but we do see a real and growing risk which means we need to take steps today to address the future possibility of a large enough quantum computer being created”, they say.
PQXDH for dummies
The official specification page for Signal’s PQXDH has mercy on us and starts gently: PQXDH stands for Post-Quantum Extended Diffie-Hellman key agreement protocol. PQXDH establishes a shared secret key between two parties who mutually authenticate each other based on public keys. PQXDH provides post-quantum forward secrecy and a form of cryptographic deniability but still relies on the hardness of the discrete log problem for mutual authentication in this revision of the protocol.
PQXDH is designed for asynchronous settings where one user (“Bob”) is offline but has published some information to a server. Another user (“Alice”) wants to use that information to send encrypted data to Bob, and also establish a shared secret key for future communication.
Follow us on Google News









Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: