Researcher stumbles across a dangerous Android flaw that bypasses the lock screen

Did you ever find a feature on your phone by accident? This writer remembers discovering that a fast scroll up from the bottom of the Pixel 2 XL screen would take me to my first home screen page when browsing other home screen pages. Yours truly now employed this shortcut all the time on the iPhone 11 Pro Max and uses it now on my Pixel 6 Pro.
Researcher stumbles across serious Android vulnerability
Sometimes, you can come across something more dangerous; something that can threaten the safety of the personal data on your phone. According to BleepingComputer, cybersecurity researcher David Schütz discovered a way to bypass the lock screen on the Pixel 6 and Pixel 5 handsets. This could allow anyone with knowledge of this method and possession of the phone to head right to the home screen.
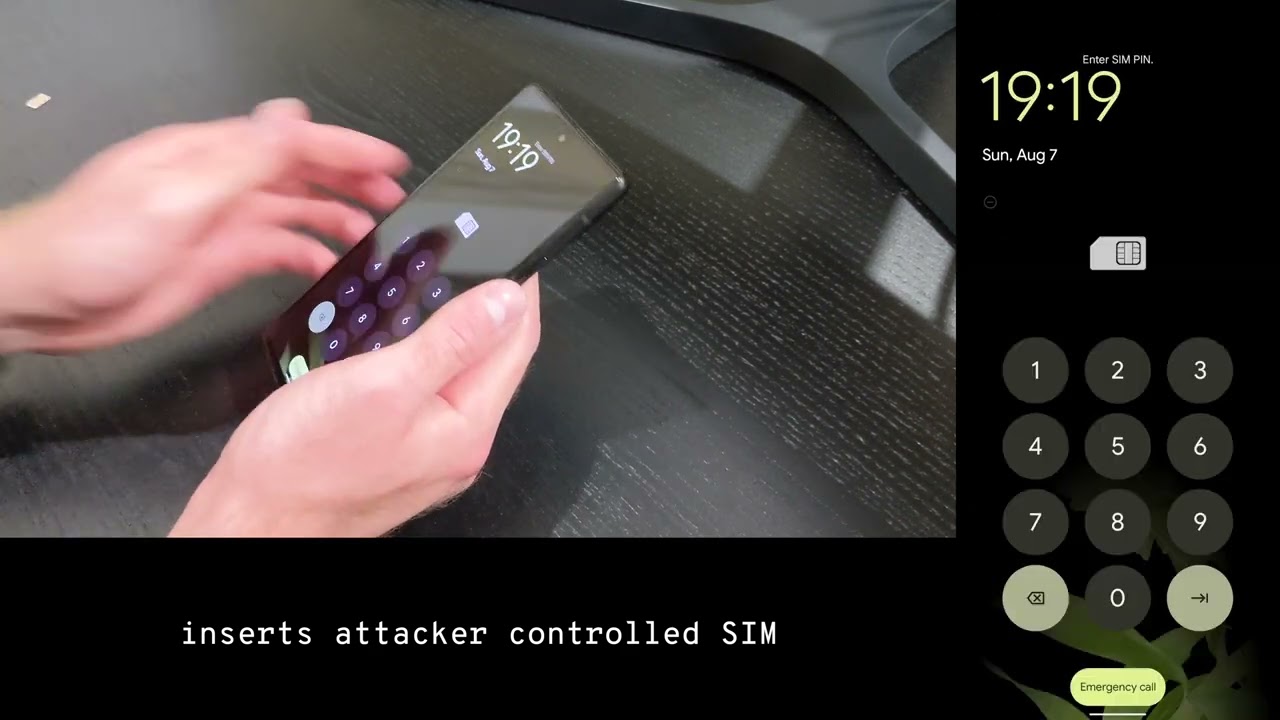

According to the report, it only takes five steps and a few minutes to use this hack. The good news is that Google patched this vulnerability in the November Android security update released on November 7th. The bad news is that the hack was available to attackers for at least six months before the patch was disseminated. But for those of you who never feel like installing a security update, these are the reasons why it is important to install each and every one.
Schütz said he discovered the flaw by accident after his Pixel 6 battery died. He entered his PIN number incorrectly three times and recovered the locked SIM card using the PUK (Personal Unblocking Key) code. The PUK is used to reset a lost or forgotten PIN number. This information can be obtained from your wireless provider. Typically, after unlocking the SIM card and selecting a new PIN number, an Android phone requests the lock screen passcode or pattern for security reasons.
But thanks to the flaw, Schütz said that his Pixel 6 requested a fingerprint scan instead which is considered unusual behavior. After playing around with the device, he found that if he started the process on his Pixel 6 when it was already unlocked, the phone would bypass the request for the fingerprint scan and allow the person holding the device to go straight to the home screen.
Android phones running these versions of the operating system are vulnerable
Phones running Android 10, 11, 12, and 13 without the November 2022 security patch remain vulnerable to the hack. Let's face it, exploiting this vulnerability does require the attacker to have possession to the targeted, unlocked phone. But if your handset has been stolen, or collected by law enforcement under subpoena, or has just gone missing, the person in possession of the device could swap the SIM card on it for the one on his phone, disable biometric authentication, enter the wrong PIN number three times, and punch in the PUK number. That person now has home screen access to your phone.
Schütz reported the vulnerability to Google this past June and the cooler temperatures and earlier sunset times should remind you that we are no longer enjoying the summer season. For his troubles, Schütz was awarded $70,000 by Google for bringing this flaw to its attention. The Alphabet unit had designated a Common Vulnerabilities and Exposures (CVE) number of CVE-2022-20465 to the flaw.
So what have we learned here? Well, we learned that playing around on your phone could help you find a vulnerability, especially if you are a cybersecurity researcher. We learned that it is important to install security updates as soon as they are available (usually the first Monday of every month for Android handsets). And we also learned that sometimes it is better to be selfish and refuse to lend your phone to someone claiming that they need to make a call, even an emergency call.
Sorry to be so harsh, but there have been cases when someone has asked to make a call for emergency purposes and then ran off with the Good Samaritan's handset. If there is an emergency, you can tell the person that you will make the call on his behalf.










Things that are NOT allowed: