Pixel vulnerability that hits the Markup screenshot editing tool is potentially dangerous
Tomorrow, Pixel 6 users should be able to install the stable version of QPR2 which includes the March security patch. And while those who installed the QPR3 Beta 1 update (like yours truly) already have the March security patch, the rest of those using the Pixel 6 series will be covered from a nasty vulnerability that allows a bad actor with knowledge of only a phone number to access incoming and outgoing data via a flaw in the Exynos modem chip used on these devices.
Another vulnerability is patched by the March security patch although merely installing the update won't make all of your problems go away. As per 9to5Google, reverse engineers Simon Aaarons and David Buchanan discovered a flaw dubbed "aCropalypse" that affects the Pixel's own screenshot editing tool which is known as Markup. The flaw could allow a bad actor to reverse edits made of PNG screenshots in Markup.
Markup was released as part of Android 9 Pie in 2018 and allows users to crop, draw, add text, and highlight screenshots. As an example, let's say you took a screenshot of your credit card from your bank's website. You crop out everything except for the card number that you cover up using the black marker tool available via Markup. If you share this image on certain platforms, the vulnerability can allow the attacker to see most of the original, unedited screenshot before it was cropped or edited.
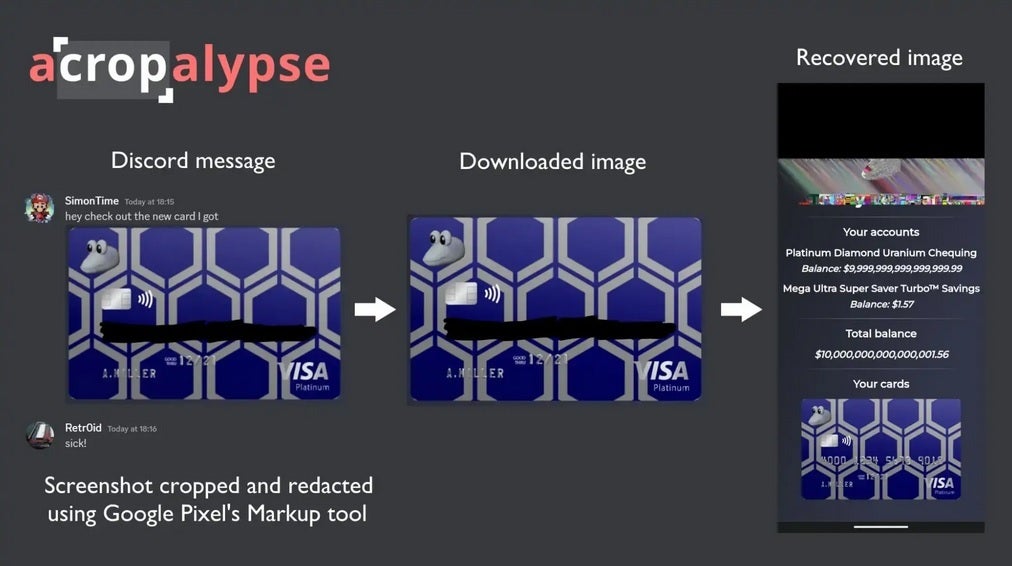
Example of how the aCropalypse flaw can expose personal information from an edited screenshot
In other words, the edits can be reversed and the black lines covering the card's account number will disappear revealing the information that was hidden. In fact, 80% of the screenshot can be recovered possibly allowing other personal information such as addresses, phone numbers, and other private data to be viewed.
This occurs because Markup saves the original pre-edited, pre-cropped screenshot in the same file location as the edited screenshot and never deletes the original image. Some platforms such as Twitter will reprocess the image which removes the flaw, Discord, didn't patch its site until January which means images posted on the platform before January 17th could be vulnerable.
The flaw was designated in the March security patch as CVE-2023-21036. CVE stands for Common Vulnerabilities and Exposures and is used to identify, catalog, and promote flaws.
There is a website that you can use at acropalypse.app (or tap on this link) to determine whether a screenshot you previously shared can be exploited. Considering that this vulnerability first surfaced as long as five years ago, you might have some shared screenshots that you edited to hide certain information. The hidden data could be at risk depending on the platform you shared it on even after you install the March security update on your Pixel phone.










Things that are NOT allowed: