Report details a dangerous Android phishing campaign that can take control of your phone

Mobile security company Zimperium (via BGR) has come across spyware aimed at Android users in South Korea that is called PhoneSpy. Over 1,000 South Korean Android users have been victimized by this collection of spyware apps that disguise themselves as useful tools for Android users. The spyware gives the bad actors behind PhoneSpy access to the data, communication, and services on victims' handsets.
PhoneSpy apps hide as useful apps in plain sight
What makes it hard to find PhoneSpy apps is that they hide in plain sight. These apps pretend to be helpful, teaching users how to do Yoga, stream television shows and videos, and browse the photos on your phone.
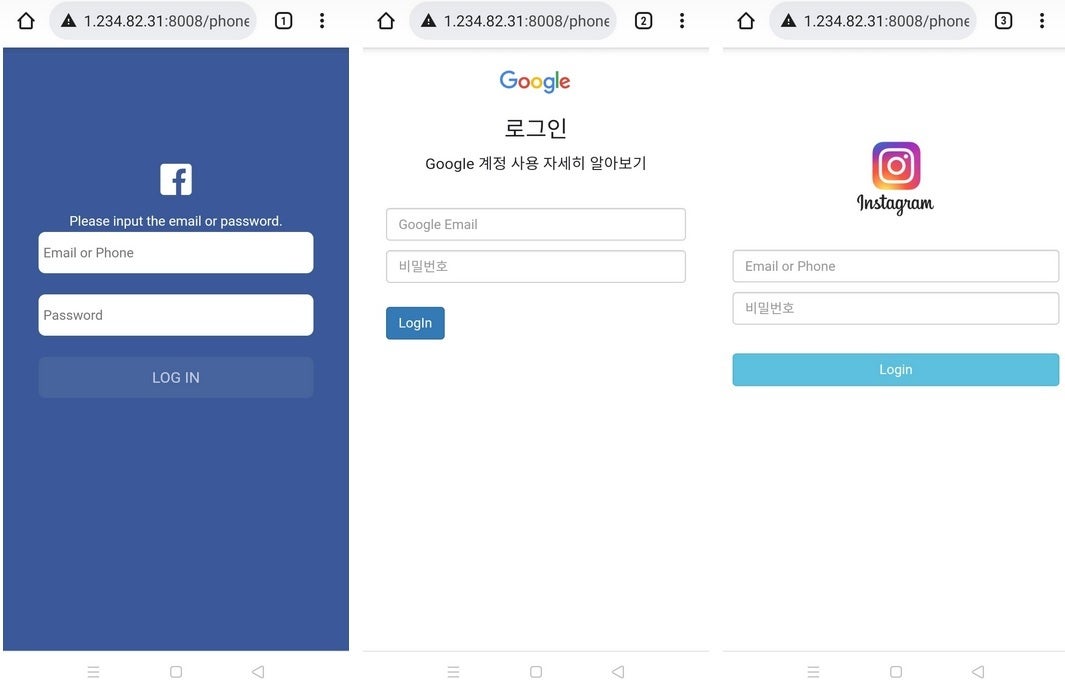
These look real but are really phish looking to capture login information that can be used to steal data
Zimperium says, "But in reality, the application is stealing data, messages, images, and remote control of Android phones. The data stolen from victim devices ranged from personal photos to corporate communications. The victims were broadcasting their private information to the malicious actors with zero indication that something was amiss."
Right now, victims of PhoneSpy have been limited to mobile users living in South Korea. When these apps are installed on Android phones, they put users' personal and corporate data at risk. And as smartphones and tablets are becoming deployed more and more by companies to their stay-at-home workers, spyware is being used to take control of many devices.
Once PhoneSpy is installed, it can be used to take control of the camera on an Android phone, record audio and video, use the GPS to get the precise location of the device, view pictures taken with the device's camera, and more. The spyware was not discovered on any app in any App Store which indicates that the bad actors are "redirecting web traffic" or using "social engineering." The latter is a method used by attackers to manipulate victims into acting certain ways (tapping certain links) and divulging certain information.
According to Zimperium's report, PhoneSpy spyware can do the following:
- Complete list of the installed applications.
- Steal credentials using phishing.
- Steal images.
- Monitoring the GPS location.
- Steal SMS messages.
- Steal phone contacts.
- Steal call logs.
- Record audio in real-time.
- Record video in real-time using front & rear cameras.
- Access camera to take photos using front & rear cameras.
- Send SMS to attacker-controlled phone number with attacker-controlled text.
- Exfiltrate device information (IMEI, Brand, device name, Android version).
- Conceal its presence by hiding the icon from the device’s drawer/menu.
PhoneSpy uses phishing attacks to gather more personal data from victims
After the PhoneSpy spyware is installed, it opens a phishing page that imitates the login page of popular South Korean messaging app "Kakao Talk" in order to steal credentials. And like any app, it seeks permissions to use certain features of a phone.
While it isn't clear whether there are connections between victims, the spyware can download contact lists and send SMS messages supposedly from the victim. As a result, the report says that "there is a high chance that the malicious actors are targeting connections of current victims with phishing links."
There is some good news. Zimperium says that its zLabs mobile threat research team found just 23 Android apps being used in the PhoneSpy campaign. And as previously noted, the campaign appears to be targeted at South Korean phone users. The bad news is that it seems that thousands of victims in the country installed malicious apps.
Perhaps the best early warning sign that you can use is the comments section for any listing inside any app store. That is where you will find the red flags about adware and other apps that give control of your phone to a bad actor.










Things that are NOT allowed: