NSA: Doing this to your phone once a week can protect it from a malicious attacker

The National Security Agency (NSA) published a mobile device best practices guide in 2020. In the guide, the agency said, "many of the features (on a phone) provide convenience and capability but sacrifice security." The NSA guide revealed the simple steps that smartphone owners can take to improve their phone's defense against attacks. Some of these are nothing more than common sense approaches such as the use of strong passwords and PINs.
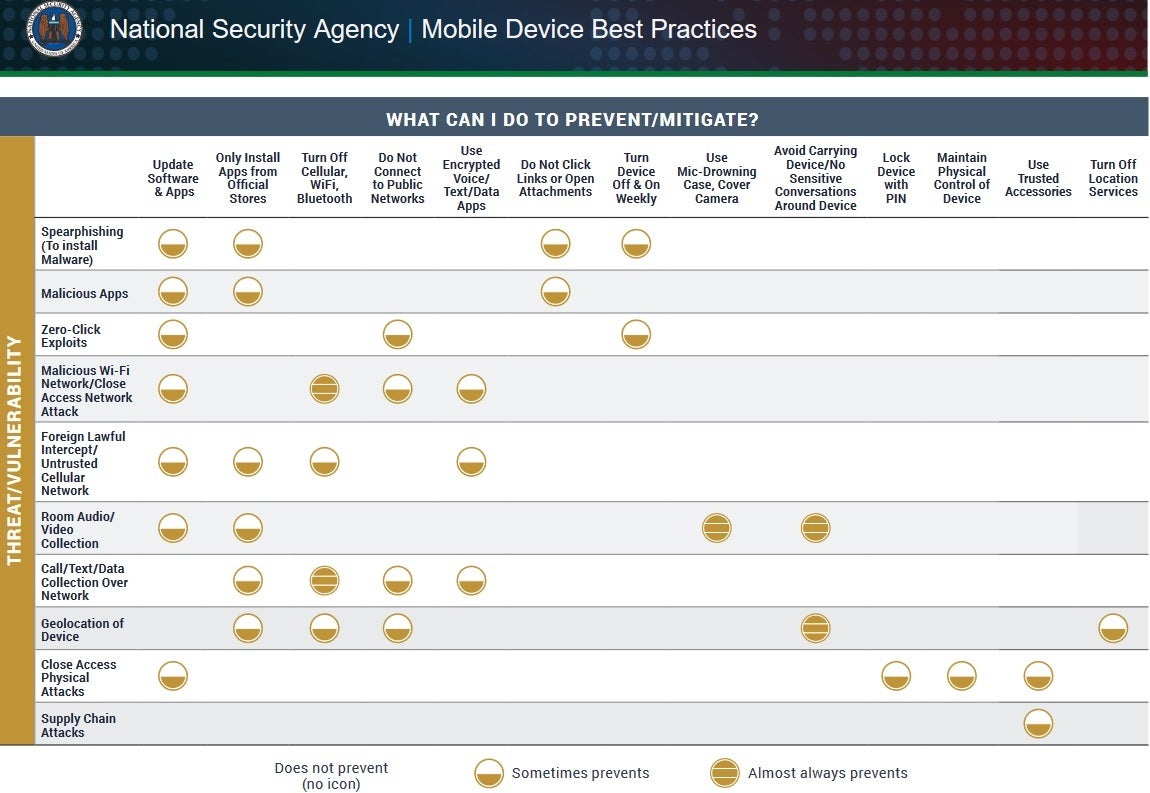
Other simple security boosting steps include using biometric protection such the use of a fingerprint sensor or a facial recognition system. In addition, you should always update your device so that it is running on the most recent software update released. The guide also warns iOS and Android users not to jailbreak or root their phones, not to click on unknown links (this one is a biggie!), nor should you open unknown attachments. And the NDA recommends that iOS and Android users turn their phones off and back on at least once each week.
The NSA's smartphone document noted that regularly rebooting your device will sometimes prevent an attack known as spear phishing. This goes beyond a regular phishing attack where a bad actor sends an email or text designed to appear as though it was written by and sent from a trusted source. A spear phishing attack is more personal and the faked email is "highly personalized" and created with the specific target in mind.
The NSA's Mobile Device Best Practices. | Image credit-Forbes
Weekly rebooting can sometimes deflect a zero-click attack. This is an attack on a device that doesn't require the user of the phone to perform any specific action to exploit a vulnerability. The attacker can take control of a device without the device user having to click on a link, open a file, or take any other action.
It is important to note that while the NSA believes that a weekly reboot can sometimes prevent you from becoming the victim of a malicious attack, the recommendation was not made as a surefire solution. One action you can take that will work all of the time against a malicious Wi-Fi network, a close access network attack, and the collection of call, text, and data over a network is to disable your device's cellular, Wi-Fi, and Bluetooth connections. That is obviously not a practical solution.
Check the chart that we've embedded in this article to see other NSA-suggested actions you can take including the one that suggests you do not connect to public networks. Heeding such advice will sometimes prevent zero click exploits, attacks from a malicious Wi-Fi network, a close access network attack, the collection of calls, texts, and data over a network, and the discovery of where the device is located.










Things that are NOT allowed: