New Android threat sends your photos, texts, contacts, hardware data and more to a foreign server

Earlier today we told you about five Android dropper apps carrying the Anatsa banking trojan that you need to delete from your Android phone if you downloaded any of them on the device. To put it simply, these apps could infiltrate your bank account without your knowledge and make unauthorized payments from the account. And if that isn't enough for Android users to worry about, another malware threat is getting press.
According to Bleeping Computer, a new version of the XLoader malware (aka MoqHao) is making the rounds. Previously, this malware was spotted in the U.S., U.K., Germany, France, Japan, South Korea, and Taiwan. The malware is disseminated through SMS text messages that feature a shortened URL link and XLoader can launch immediately after installation. This allows the malware to run undetected in the background while personal data is stolen away.
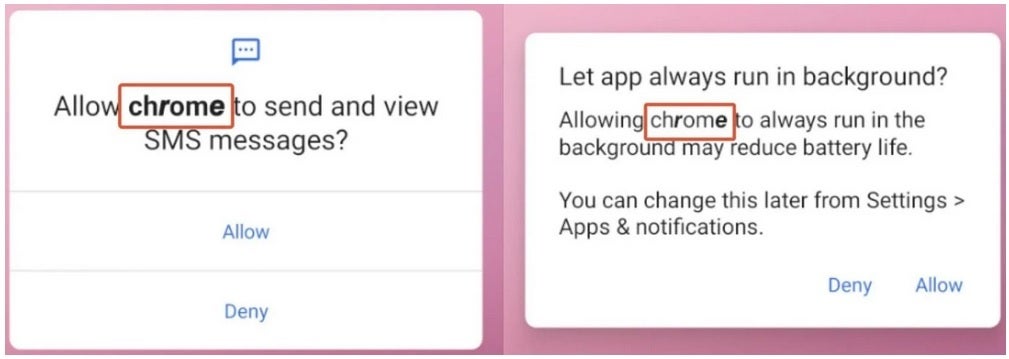
Fake permission requests are made to look like they are coming from Google Chrome
McAfee says, "While the app is installed, their malicious activity starts automatically. We have already reported this technique to Google and they are already working on the implementation of mitigations to prevent this type of auto-execution in a future Android version."
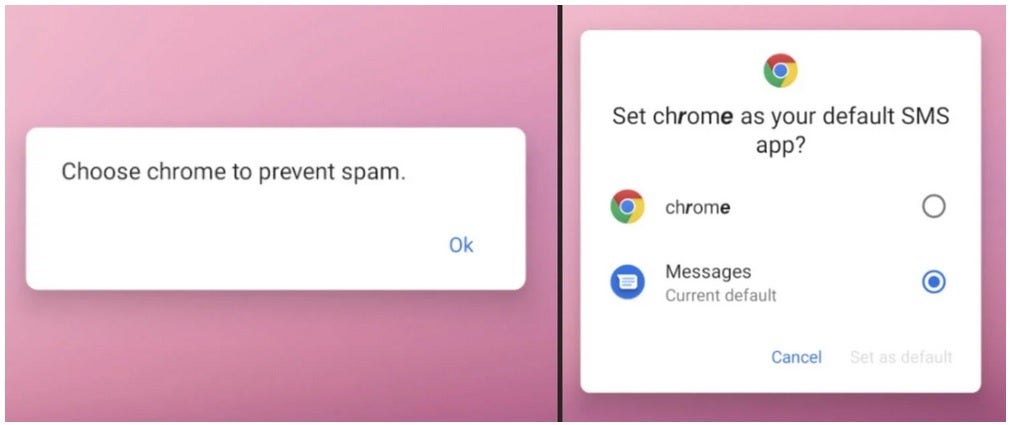
Another fake request for permission
The malicious apps send out permission requests pretending to come from Google Chrome requesting permission to send and view SMS (text) messages and asking permission to keep "Chrome" running in the background. And the coup de grace is permission to make "Chrome" your default SMS app. The malware, once it gets all of these permissions, is used to send photos, text messages, contact lists, and info on the hardware you are using (including your phone's unique IMEI number) to the control server. Yes, it is very scary.
McAfee says that since minimal interaction is required by the victim, the new XLoader malware is even more dangerous than its predecessor. There is some good news. An update from McAfee dated a couple of weeks ago says that Android devices with Google Play Services are protected from attacks from this kind of malware by Google Play Protect which is enabled by default.
Still, there are some takeaways to consider here. Never click on a shortened URL found in a message. And never sideload an app.










Things that are NOT allowed: