Delete these malicious Android apps now before they log-in to your Facebook account
Security firm Trend Micro has discovered some optimizer and utility apps that were listed in the Google Play Store that could load as many as 3,000 different variants of malware on an infected phone. These apps have been installed a total of 470,000 times. Google has already removed the malicious apps from the Play Store although they could remain installed on Android phones.
We usually suggest that Android users check out the comment section in the Google Play Store before installing an app from an unknown developer. This way you might be able to find red flags from Android users warning you to stay away. However, the bad actors who developed this malware can use it to hijack an infected device and post positive reviews for the malicious apps. A screenshot from one of the apps shows several positive comments from different users, but all of them have the same comment! If you see something like this in the Play Store comment section, do not install that app. These apps can also run ads and have the infected device click on them to help the criminals behind the enterprise get paid. And the malware has the ability to log-in to a victim's Google and Facebook accounts.
Without icons on the app launcher, this malware is hard to uninstall or even discover
The 3,000 variants of malware or malicious payloads disguise themselves as system applications so there are no icons on the launcher or the app list. Thus, the user might not even know that his/her phone is infected. And if he or she does figure it out, uninstalling the app is going to be quite difficult. The apps trick users into enabling certain Android permissions and disabling Google Play Protect which is supposed to scan for malware on Google Play Store apps before they are installed.
The countries most impacted by this campaign were Japan, Israel, Taiwan, the U.S., India, and Thailand. The affected apps include:
| Name of app | Package | Installs |
|---|---|---|
| Shoot Clean-Junk Cleaner, Phone Booster, CPU Cooler | com.boost.cpu.shootcleaner | 10,000+ |
| Super Clean Lite- Booster, Clean&CPU Cooler | com.boost.superclean.cpucool.lite | 50,000+ |
| Super Clean-Phone Booster,Junk Cleaner&CPU Cooler | com.booster.supercleaner | 100,000+ |
| Quick Games-H5 Game Center | com.h5games.center.quickgames | 100,000+ |
| Rocket Cleaner | com.party.rocketcleaner | 100,000+ |
| Rocket Cleaner Lite | com.party.rocketcleaner.lite | 10,000+ |
| Speed Clean-Phone Booster,Junk Cleaner&App Manager | com.party.speedclean | 100,000+ |
| H5 gamebox | com.games.h5gamebox | 1,000+ |
| LinkWorldVPN | com.linkworld.fast.free.vpn | 1,000+ |
Another report, this one from Cofense (via ArsTechnica) reveals that a phishing scam is leading unaware Android users to download apps containing malware called Anibus. The bad actors send out attachments that appear on the surface to be invoices. Instead, they are actually APKs used to install malware-loaded Android apps. Users who download the fake invoices and allow their phones to sideload apps will see a fake Google Protect message that asks for two privileges; the latter disables Google Play Protect and agrees to 19 permissions. The malware then scans an infected device looking to see if it has any of 263 banking and financial apps installed. If one of these apps is loaded on a phone, when the user opens it a fake log-in page is displayed allowing the attackers to steal the passwords for these apps.
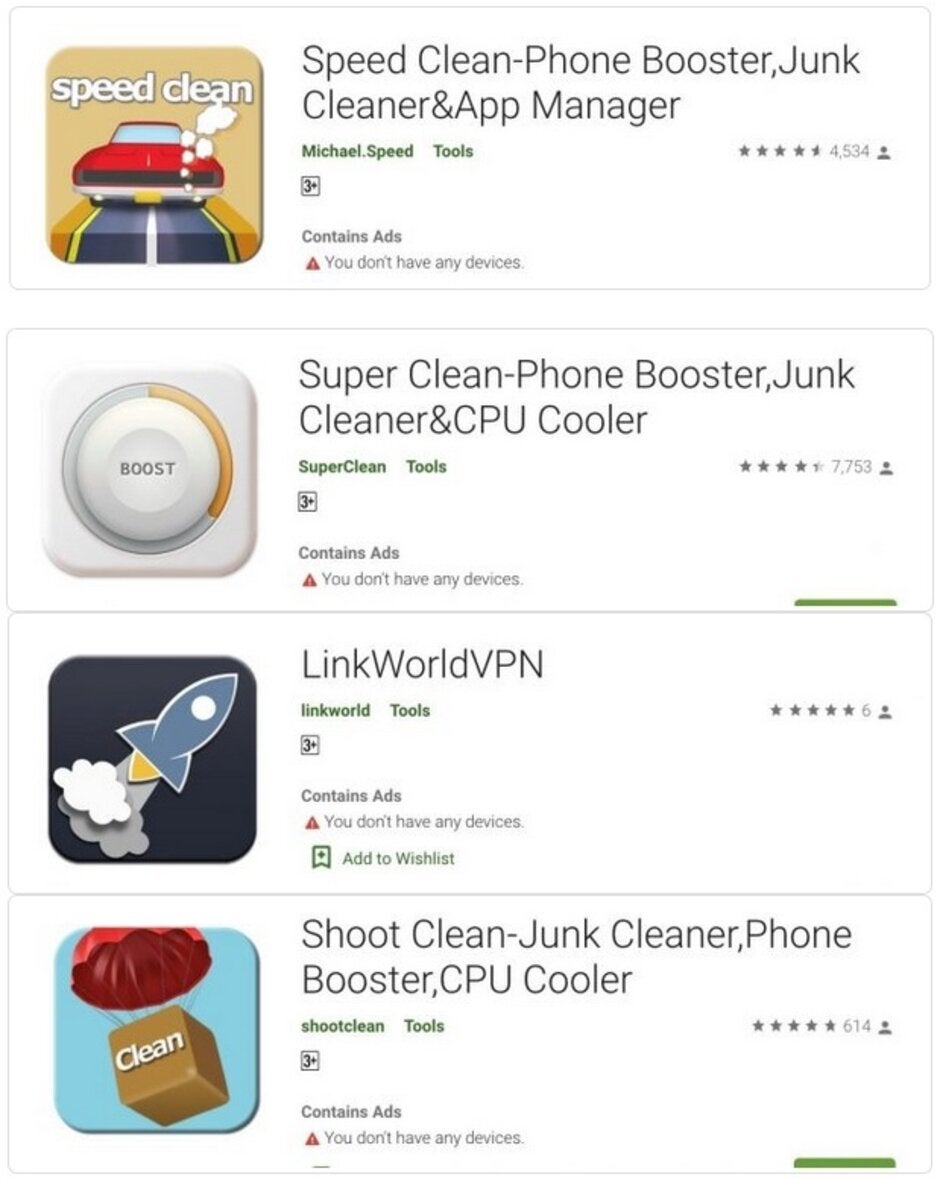
Some of the malicious apps that delivered malware to infected Android phones
Other things that Anubis can do includes capturing screenshots, changing settings, opening and visiting any URL, recording audio, making calls, stealing the contact list, sending texts, receiving texts, deleting texts, locking the device, getting the user's location via GPS, looking for files, encrypting files on the device and external drives, grabbing remote control commands from Twitter and Telegraph, pushing overlays on the screen and stealing the ID of a particular device.
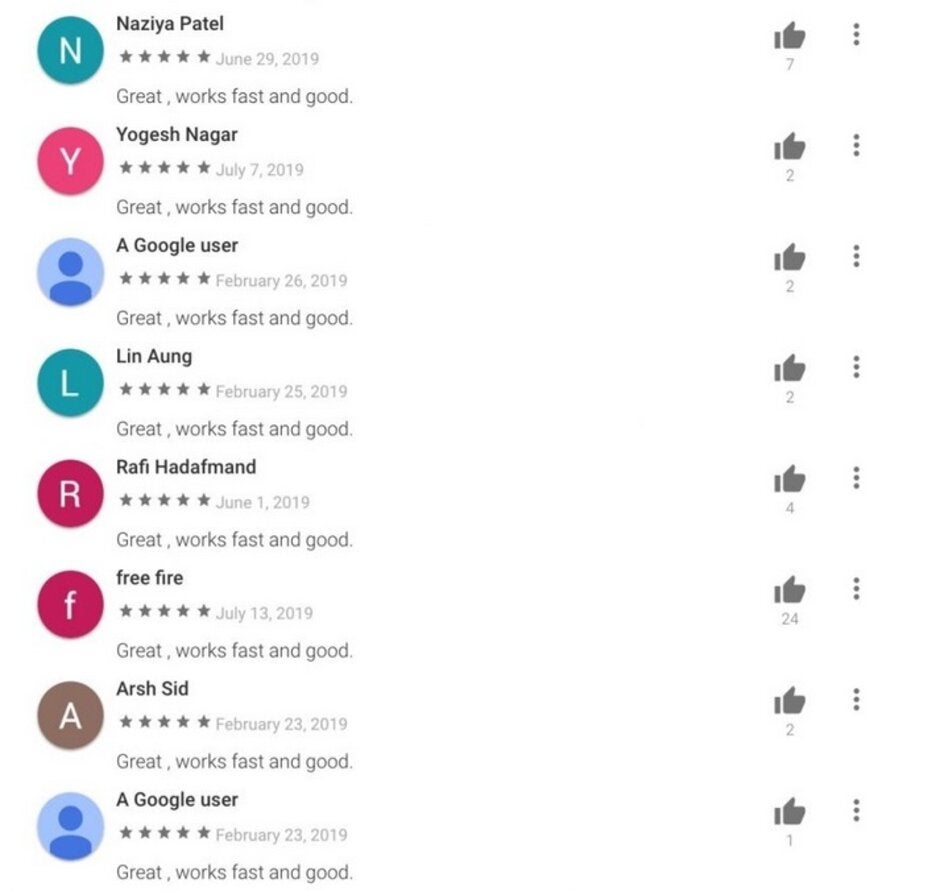
The malware allowed the attackers to write positive reviews, but they weren't too smart
And once the attacker is done with the infected phone, he can remotely "destroy it." A researcher with security firm Cofense wrote, "For example, once the attacker has harvested and exploited all the credentials, contacts, emails, messages, sensitive photos, etc., they might choose to encrypt the phone for a ransom or simply destroy the phone out of malice."
These examples make it clear that smartphone users need to restrict the apps they install to those produced by developers they know of. And if a user receives an email or text message asking him to download an invoice in the form of an attachment, he should call the company first to make sure it is real.










Things that are NOT allowed: