Four zero-day flaws are exploited as iPhone units are loaded with Spyware

According to ArsTechnica, researchers today presented evidence showing that over four years as many as thousands of iPhone units were attacked by spyware. These iPhones were owned by employees of security firm Kaspersky in Moscow. The attackers were able to obtain a level of access never seen before and it was all done by exploiting a vulnerability in a hardware feature that not too many outside of Apple and semiconductor design firm Arm Holdings were familiar with.
It isn't known how the attackers learned about this hardware feature and even the researchers have no idea what purpose it had. Also unknown is whether the hardware was a native iPhone part or enabled by a third-party component such as Arm's CoreSight. In addition to infecting iPhone units belonging to Kaspersky employees, the spyware also affected the iPhones that were used by thousands of people working in embassies and diplomatic missions in Russia.
How was the spyware disseminated to target iPhones? It apparently was sent through iMessage texts using a process that did not require the victim to take any action. Once infected, the iPhones transmitted microphone recordings, photos, geolocation data, and other sensitive information to servers controlled by the attackers. While rebooting an iPhone would rid the device of the infection, the attackers would send a new text loaded with spyware to the same device and re-infect it every time it was rebooted.
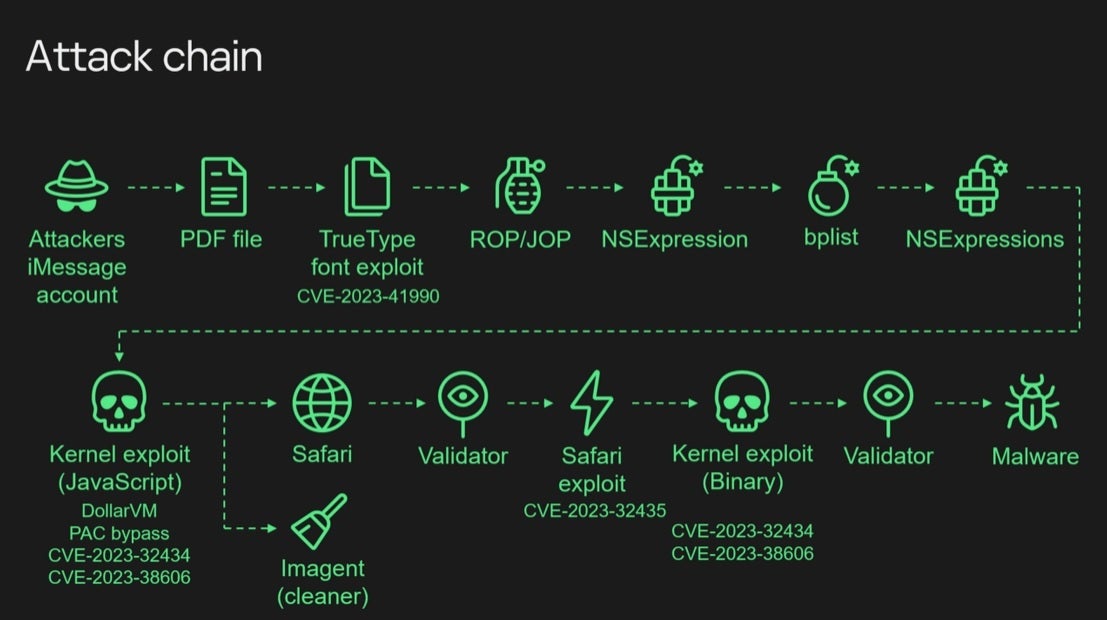
The Triangulation exploit chain
In an email, Kaspersky researcher Boris Larin wrote, "The exploit's sophistication and the feature's obscurity suggest the attackers had advanced technical capabilities. Our analysis hasn't revealed how they became aware of this feature, but we're exploring all possibilities, including accidental disclosure in past firmware or source code releases. They may also have stumbled upon it through hardware reverse engineering."
The malware and the campaign that led to the installation of it were both called "Triangulation" and it contained four zero-day vulnerabilities which means that the attackers knew about these vulnerabilities before Apple did. Apple has since patched the flaws which were cataloged as:
- CVE-2023-32434
- CVE-2023-32435
- CVE-2023-38606
- CVE-2023-41990
The aforementioned secret hardware at the root of this issue and the four zero-day flaws not only affected iPhone models, it also impacted iPads, iPods, Macs, Apple TVs, and Apple Watches. Apple patched the vulnerabilities on all of the above-mentioned devices.
In a press release, Kaspersky's Larin added, "This is no ordinary vulnerability. Due to the closed nature of the iOS ecosystem, the discovery process was both challenging and time-consuming, requiring a comprehensive understanding of both hardware and software architectures. What this discovery teaches us once again is that even advanced hardware-based protections can be rendered ineffective in the face of a sophisticated attacker, particularly when there are hardware features allowing to bypass these protections."
As for who was behind the attack, some blame the U.S. National Security Agency (NSA). Russia's Federal Security Service says the attack came from the NSA working with Apple although Kaspersky said that it has no evidence that either were involved.
Follow us on Google News









Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: