"Scary" vulnerability found in the iPhone/iPad Mail app; Apple says patch is coming soon

Apple acknowledged today that there is a vulnerability in the iOS mail app that hackers might have exploited. The company says that it is working on a software fix to get rid of this flaw and a software update will be disseminated soon. In fact, a patch was discovered on the iOS 13.4.5 beta recently released to developers. The issue was discovered by San Francisco mobile security firm ZecOps. The CEO of the company, Zuk Avraham, said that he found evidence that the vulnerability was exploited six times by hackers who broke into iPhones using this technique.
Vulnerabilities discovered by security firm have been around since iOS 6
The report, published today by ZecOps, says that the security company first spotted attacks on the iOS stock Mail app back in January 2018, The vulnerability existed as far back as iOS 6 with the release of the iPhone 5 in September 2012. The attacks were made on iPhone and iPad devices belonging to high-profile enterprise users, VIPs, and companies that manage cybersecurity for internet users. ZacOps says that the six attacks that were detected occurred on iOS devices belonging to individuals from a Fortune 500 organization in North America, an executive from a carrier in Japan, a German VIP, MSSPs from Saudi Arabia and Israel, a European journalist and an executive working for a Swiss enterprise.
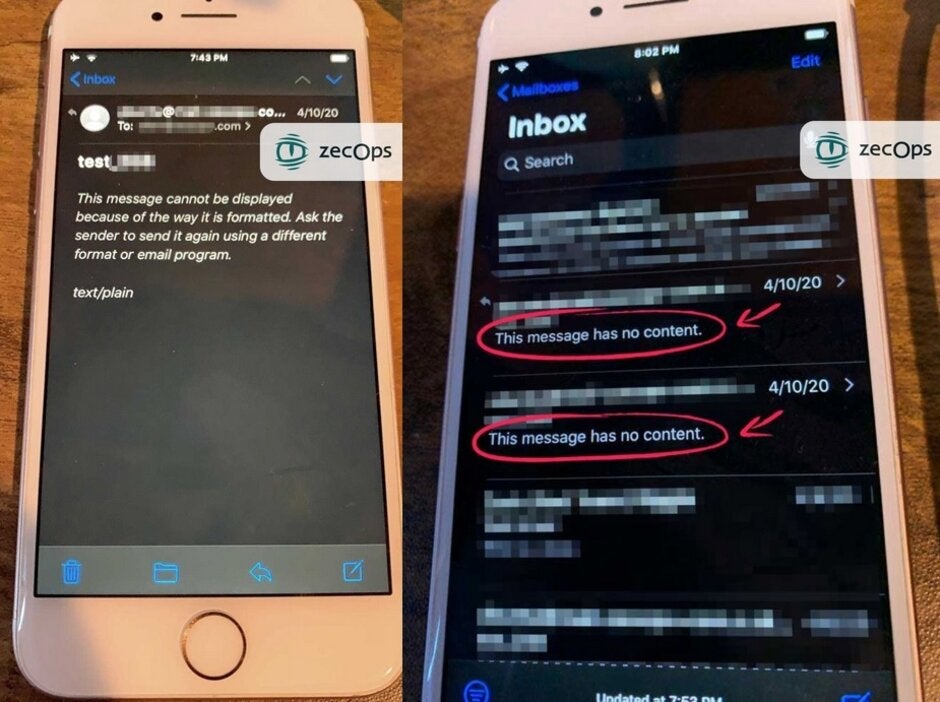
Images show the result of a failed attack
The attacks were apparently triggered through a blank email that is received on the iOS stock Mail app forcing the phone to crash and reboot. The vulnerability can be accessed before the entire email is downloaded, which means that the email used in the attack is not found on the targeted device. Attackers also send emails that consume larges amounts of memory. The email itself doesn't necessarily have to be large but can burn plenty of RAM by using Rich Text Format (RTF), multi-part (which sends both HTML and text versions of a message), and other memory consuming formats.
On iOS 13, an attack email can be received by the Mail app if it is running in the background. With iOS 12, the user must click on the attack email; however, if the attacker has control of the mail server, a zero-click attack can be made on iOS 12. If the attack hits your phone, you will see a temporary slowdown in the Mail app but nothing else. Attacks that fail have a message that reads, "This message has no content."
The security firm says that these bugs alone cannot allow a hacker to take full control of an iPhone or iPad without "an additional infoleak bug & a kernel bug." However, even without these additional bugs, a successful attack can allow a hacker to leak, modify, and delete emails in the target's inbox.
Avraham discovered the attacks by studying crash reports and recreating them to see what caused the crash. Reuters spoke with two independent security firms who found the information presented to them credible but had not yet recreated the exploits. Apple security expert Patrick Wardle, a former researcher for the U.S. National Security Agency, said that the discovery of this vulnerability "Confirms what has always been somewhat of a rather badly kept secret: That well-resourced adversaries can remotely and silently infect fully patched iOS devices."
Another security researcher, Bill Marczak with Citizens Lab, called ZacOps' report "scary." He added, "A lot of times, you can take comfort from the fact that hacking is preventable. With this bug, it doesn’t matter if you’ve got a PhD in cybersecurity, this will eat your lunch."
As we pointed out earlier in this article, Apple will patch this vulnerability with the iOS 13.4.5 update. Even if you don't like to update your phone right away when a new build of iOS is dropped, you might want to make an exception with iOS 13.4.5.












Things that are NOT allowed: