Apple releases iOS 17.1.2, iPadOS 17.1.2 to patch two serious Zero-day vulnerabilities

Apple today released iOS 17.1.2, and iPadOS 17.1.2 to patch a pair of zero-day vulnerabilities that have already been exploited according to Apple. A Zero-day vulnerability is one that developers did not know about and can be exploited until mitigated. Both of the flaws found on iOS 17.1.2 deal with the WebKit browser engine on the iPhone XS and later, iPad Pro 12.9-inch 2nd generation and later, iPad Pro 10.5-inch, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 6th generation and later, and iPad mini 5th generation and later.
The first vulnerability might lead to sensitive information being disclosed while web content is being processed. Apple says that it is aware of a report stating that the vulnerability was exploited on versions of iOS before iOS 16.7.1. The issue was given a Common Vulnerabilities and Exposures (CVE) number of CVE-2023-42916 and was discovered by Clément Lecigne of Google's Threat Analysis Group.
Apple releases iOS 17.1.2 to patch two zero-day vulnerabilities
The flaw being patched allowed the attackers to read memory beyond the buffer allowing them to see sensitive and personal information. And we're talking about the kind of information that could lead to the emptying of the user's bank account or unauthorized use of the user's credit cards. Apple says that the out-of-bounds read was addressed with improved input validation.
The CVE number for this second vulnerability is CVE-2023-42917 and was also discovered by Clément Lecigne of Google's Threat Analysis Group. With this flaw, processing web content could lead to an arbitrary code execution allowing an attacker to run any commands or code and again, possibly stealing personal information.
And like the first CVE, this is the kind of information that could reveal certain passwords or give up other information allowing an attacker to get into your bank account or use your credit cards to purchase things that can be quickly converted to cash. The bad news here is that this vulnerability was also exploited, according to Apple, before iOS 16.7.1. Apple said that the memory corruption vulnerability was addressed with improved locking.
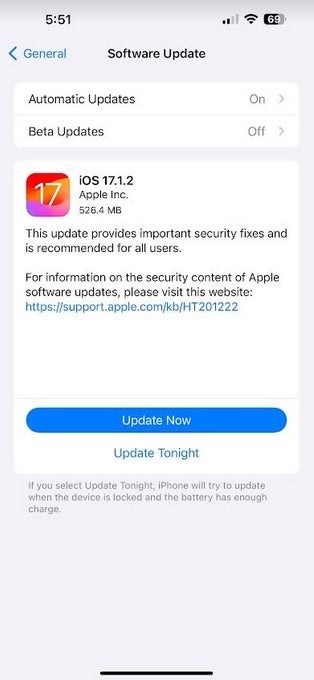
To install the update go to Settings > General > Software Update.
Follow us on Google News


![Some T-Mobile users might be paying more starting in March [UPDATED]](https://m-cdn.phonearena.com/images/article/176781-wide-two_350/Some-T-Mobile-users-might-be-paying-more-starting-in-March-UPDATED.webp)











Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: