Report reveals law enforcement's secret tool for stealing your iPhone passcode

It's one thing to use a tool that cracks an Apple iPhone passcode using brute force. With this method, a cracking tool can go through every possible combination for a six-digit passcode in hours. A couple of years ago, John Hopkins Information Security Institute professor cryptographer Matthew Green calculated that by using a GrayKey machine such a task would take as long as 11 hours. However, its another thing for a forensics tool to remember the passcode by storing it as the user types in each number digit by digit.
The FBI cracked a terrorist's iPhone by guessing the passcode
Grayshift, the company that makes the aforementioned GrayKey cracking tool, has software called Hide UI that most of the public is unaware of. According to NBC News, which cited a couple of law enforcement sources, this tool can track a suspect's iPhone passcode as soon as it is punched into the phone. The sources had to remain anonymous so as not to violate a non-disclosure agreement they had signed. Because Hide UI is unknown and kept quiet from the public, many defense attorneys and civil rights advocates are concerned that the tool could be used without a warrant violating the due process of suspects. Jennifer Granick, an attorney with the ACLU, says, "This is messed up. Public oversight of policing is a fundamental value of democracy. With these kinds of novel tools we see a real desire for secrecy on the part of the government."
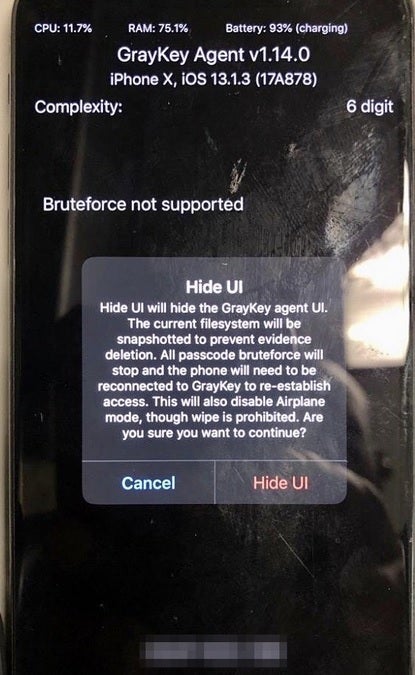
Screenshot of the Hide UI on the iPhone X
One law enforcement official familiar with the GrayKey cracking tool said that if it doesn't work, "we can move to Plan B, which is Hide UI." For Hide UI to work, the software must be installed on an iPhone and the cops have to come up with a scenario that puts the phone in the hands of the suspect without making him suspicious. One way to do this is to hand the phone back to the suspect and tell him that he can call his attorney. When the suspect hands his phone back to the cops, Hide UI will have the user's passcode stored in a file that can be extracted by the GrayKey machine.
One law enforcement official says of Hide UI, "It’s great technology for our cases, but as a citizen, I don’t really like how it’s being used. I feel like sometimes officers will engage in borderline and unethical behavior." Another law enforcement official called the software "buggy" and that it was often easier to get the suspect to hand over his passcode during interrogation than to use the trickery required for Hide UI to work.
A leaked screenshot of Hide UI installed on an iPhone X was shared with NBC News. It shows that the software not only record the user's passcode, it also disables Airplane Mode and prevents the device from being wiped.
The Hide UI is newsworthy today as the DOJ, and Attorney General William Barr announced that the FBI had broken into one of two iPhones owned by Mohammed Saeed Alshamrani. The latter shot three people at the Naval Air Station in Pensacola Florida last December and the FBI was able to crack one of the handsets revealing that the terrorist had a connection with Al Qaeda. Attorney General William Barr and FBI Director Christopher Wray both called out Apple today for not helping in the investigation. Apple essentially called Barr a liar and said that it did help law enforcement with access to the suspect's iCloud account among other things.
So the FBI must have learned a lot since 2016 when they couldn't unlock San Bernardino shooter Sayed Farook's iPhone 5c, right? Uh, not really. A person familiar with the investigation but not authorized to speak to the media said that the FBI cracked Alshamrani's iPhone by guessing the passcode.












Things that are NOT allowed: