App installed from Google Play Store was a major scam ripping off 150 Android users

An app found listed in the Google Play Store targeted web3 users by being given a name that sounded very much like the title of a real open-source protocol for connecting decentralized apps on blockchains and wallets. Discovered by security researchers Check Point Research (CPR), the app is called WalletConnect which was done by the attackers to confuse it with the legitimate WalletConnect protocol. The tile image for the app happened to be the logo for the real WalletConnect protocol.
The attackers knew who they were going after since it marketed the bogus app as a way around real-life issues with the WalletConnect protocol such as the latter's included a lack of universal support for the protocol by widely used crypto wallets. Since the real WalletConnect open-source protocol did not have an official app in the Play Store, it must have been like taking candy from a baby as more than 10,000 people installed the app.
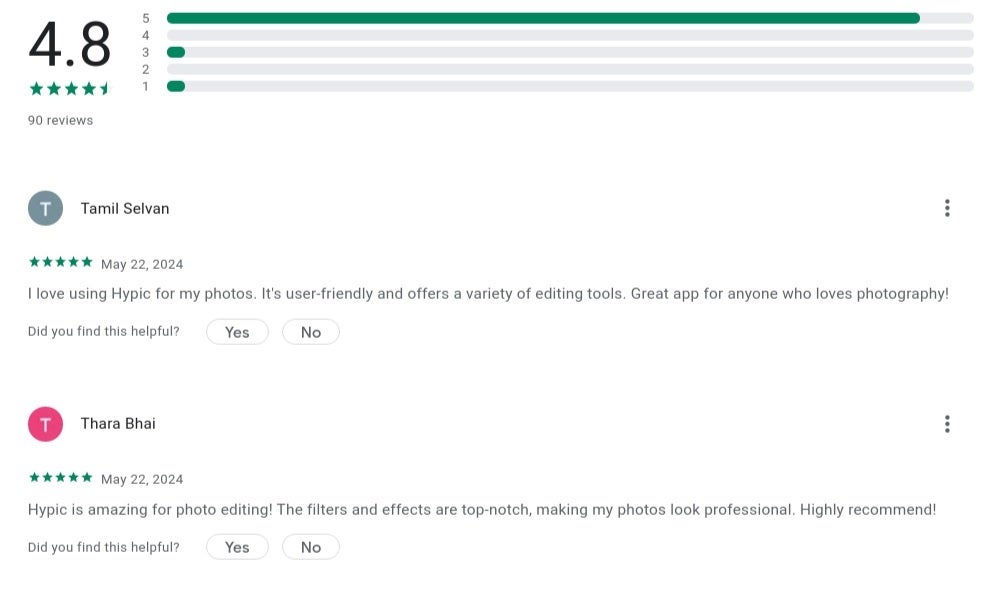
Fke reviews hiked the rating of the app and drowned out the negative reviews from victims. | Image credit-Check Point Research
While it was good that the number of those ripped off by the app was nowhere close to the more than 10,000 Android users who installed it, CPR discovered that there were over 150 addresses linked to verified transactions suggesting that this was the number of people who got hoodwinked in the scam. Once the app was installed, a new subscriber was prompted to link his or her cryptocurrency wallets, presumably loaded with cryptocurrency, to the app which users thought they could trust.
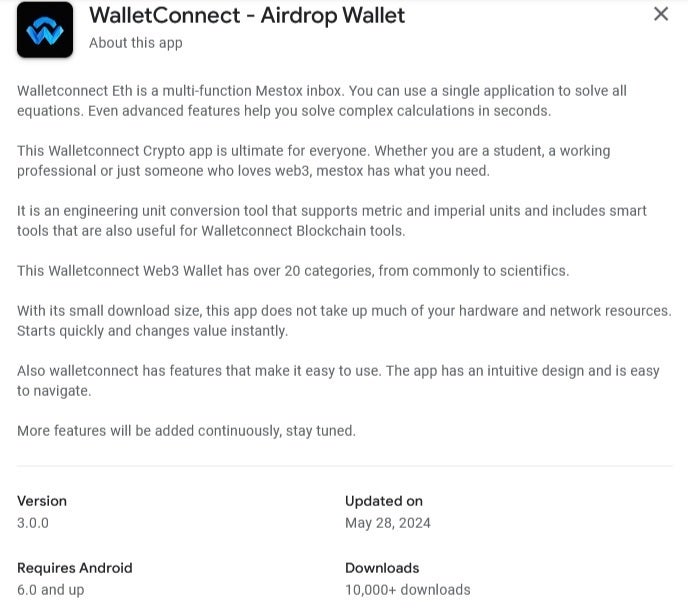
The fraudulent app's Google Play Store listing. | Image credit-Check Point Research
By linking their crypto wallets with the app, users would experience secure access to supported web3 applications. Web3 is a new iteration of the web built on blockchain technology and is controlled by the community of users. After installing the app, the users were asked to choose a new crypto wallet that supposedly supported the WalletConnect protocol. At this point, the victims were asked to authorize various transactions while also being sent to a malicious website.
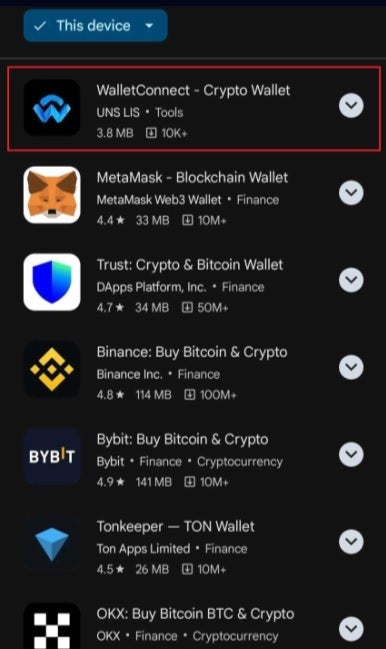
Searching for WalletConnect in Google Play would bring up the bogus app at the top of the list. | Image credit-Check Point Research
The malicious website took down all information about the victim's wallet. Using smart contracts, the attackers were able to transfer tokens from the victim's wallet into their own and even transferred more valuable crypto to themselves over less valuable kinds. According to CPR, this is the first time that a "crypto drainer" targeted mobile device users exclusively.
"Android users are automatically protected against known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play."-Google spokesman
Interestingly, only 20 victims decided to write a negative review about the app in the Play Store. This allowed the bad actors behind the scam to post tons of positive reviews to outnumber the poor reviews. The app was launched in March but was allowed to stay up for five months before it was removed from the Play Store by Google, but not before $70,000 in crypto was stolen from those who chose to install WalletConnect from the Play Store. If you did install the app, uninstall it immediately.
Follow us on Google News










Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: