Criminals spread malware by getting Android users to install fake versions of popular apps
Cybersecurity firm Bitdefender points out that one of the things that separates the Google Play Store from the App Store is also a problem for Android users. While both Apple and Google collect as much as a 30% cut of in-app revenue that is run through their respective in-app payment platforms, iOS users are forced to make their in-app purchases through Apple since Apple prevents developers from offering an alternative payment platform.
Epic offered its customers an alternative payment platform, violating Apple's rules. This is why Epic's big hit game Fortnite was kicked out of the App Store.
TeaBot malware can take full control of Android devices
Unlike App Store customers, Android users are technically not forced to make in-app purchases through Google. That's because the Play Store is not a walled garden like the App Store is and Google allows Android users to sideload apps from a third-party app store. However, by tricking Android users to use such third-party app stores, criminals are persuading Android users to install apps that most likely haven't been properly vetted leading to the spread of malware.

Fake Ad Blocker app helps to distribute the TeaBot malware
Bitdefender cites two new banker trojan malware programs called TeaBot and Flubot that help trick Android users into installing what they think are legitimate apps from popular and well-known brands but turn out to be malware-infested. Bitdefender recently found five new malicious Android apps that contain the TeaBot trojan and imitate legitimate Android apps that are popular with at least one app having been installed over 50 million times.
The cybersecurity firm discovered that the infected TeaBot apps use fake Ad Blocker apps to distribute malware. The fake apps ask permission to display over other apps, show notifications, and install apps outside of the Play Store. Once these apps are installed, their icons are hidden.
Make no mistake about it, TeaBot has the potential to do some serious damage including "overlay attacks via Android Accessibility Services, intercept messages, perform various keylogging activities, steal Google Authentication codes, and even take full remote control of Android devices."
While TeaBot is dropped by an app pretending to be an ad blocker, Flubot is spread through SMS spam and according to Bitdefender, "It steals banking, contact, SMS and other types of private data from infected devices while sporting an arsenal of other commands available, including the ability to send an SMS with content provided by the CnC."
Flubot imitates shipping apps like DHL Express Mobile with over 1 million installs from the Google Play Store, Fedex with over 5 million Android installations, and Correos with over 500,000 downloads.
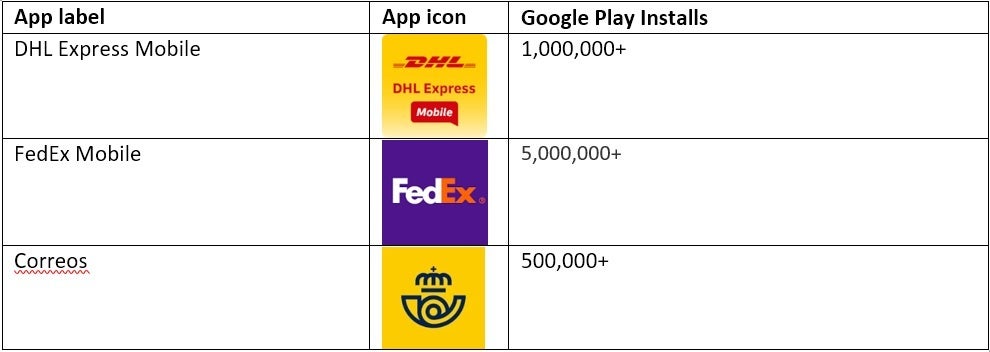
Flubot imitates shipping apps like Fedex and DHL
There is actually a way to protect yourself from having this malware infect your phone. Bitdefender suggests that you never, ever sideload apps on your device, In other words, stick to the App Store and the Google Play Store when installing apps for your iOS and Android devices respectively. Also, you should never tap on links in messages, and "always be mindful of your Android apps' permissions."
Flubot is spread through SMS spam
The fake apps containing the TeaBot payload are designed to look like the real thing although some of them have small changes in their label name and icon. For example, the real version of streaming television app Pluto TV has a label that reads "Pluto TV-it's free TV." The fake and infected version of the app has no space between Pluto and TV and reads "PlutoTV."
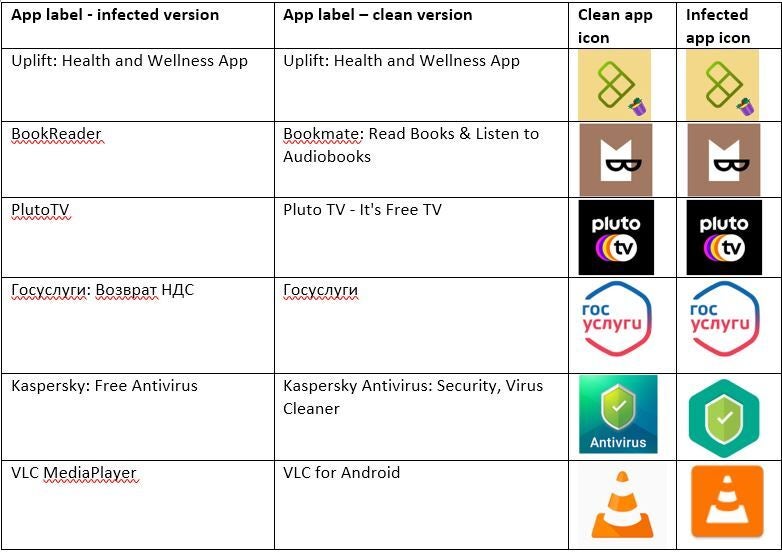
Make sure that you don't have the infected version of these apps on your phone
Nearly 93% of the fake apps trying to distribute TeaBot come from an app called MediaPlayer that tries to imitate one of the most popular titles in the Google Play Store, VLC. The latter is a "free and open source cross-platform multimedia player" with over 100 million installations. Note the big difference in the icon between the clean and infected versions of the app.
79.5% of Teabot malware has been discovered in Spain with 11.18% disseminated in Italy and 4.6% distributed in the Netherlands.










Things that are NOT allowed: