Android users need to delete these dangerous apps that managed to fool Google

Two potentially dangerous apps with a considerable number of downloads have been removed from Google's Play Store, report cyber security experts Fox-IT (via BleepingComputer).
Mister Phone Cleaner and Kylhavy Mobile Security antivirus apps were collectively installed 60,000 times and their aim was to steal banking logins by installing an evolved version of the notorious SharkBot malware.
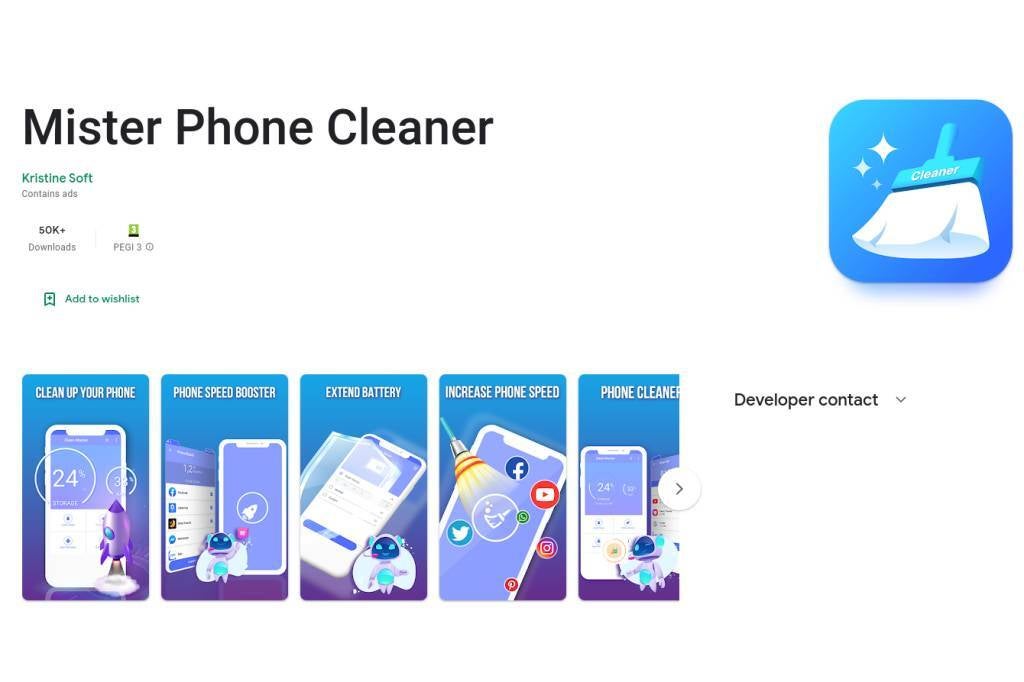
The apps initially made it to the app store because they did not contain any malicious code that would have caused Google to reject them. Mister Phone Cleaner and Kylhavy Mobile Security are dropper or helper apps, created to deliver malware to Android phones.
Once they were installed, users were prompted to install an update to stay protected against threats, which in effect was a way to install SharkBot on the victim's phone.
Although these apps are no longer available on the Play Store, users who downloaded them previously must delete them from their phones or risk consequences.
SharkBot dropper apps want to steal banking info
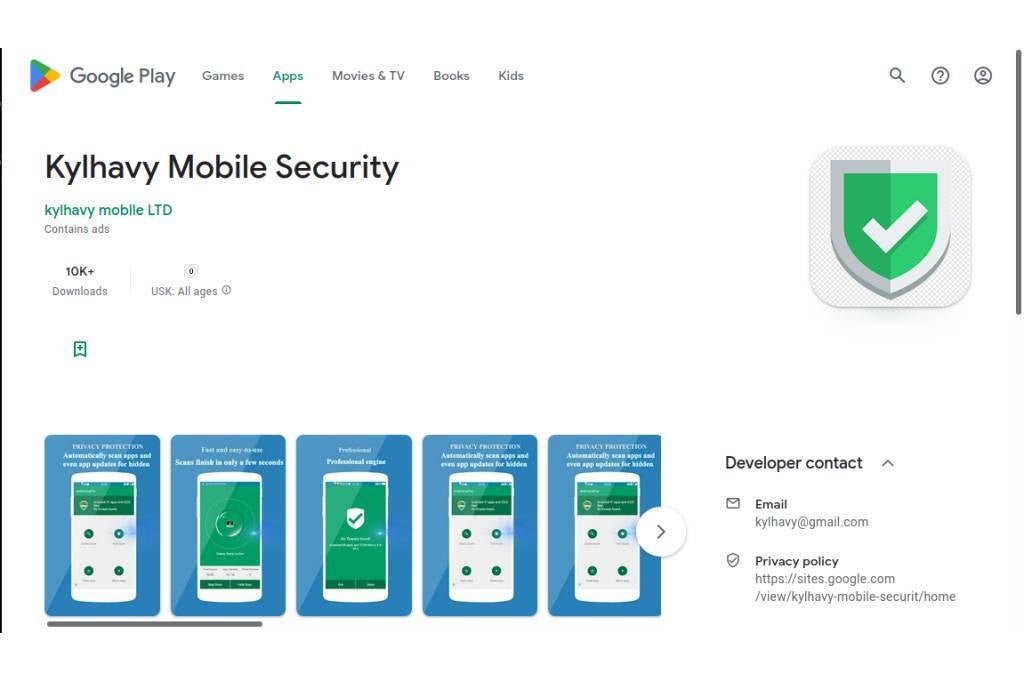
SharkBot was first discovered in late 2021 and the first apps with it were found on the Play Store in March of this year. The mode of operation at that time was to steal information through keylogging, intercepting text messages, tricking users using screen overlay attacks into divulging sensitive info, or giving cyber criminals remote control of the infected device by abusing the Accessibility Services.
An upgraded version called SharkBot 2 was spotted in May and on August 22, Fox-IT stumbled upon version 2.25 which is capable of stealing cookies from bank account logins. The newly discovered apps with SharkBot 2.25 don't abuse Accessibility Services and also don't require the Direct Reply feature as these could have made it harder for them to get approved for the Play Store.
They instead ask the command-and-control servers to directly receive the Sharkbot APK file. After that, the dropper apps notify the user of an update and ask them to install the APK and allow the required permissions.
To avoid automated detection, SharkBot saves its hard-coded configuration in encrypted form.
Using the cookie logger, SharkBot siphons off valid session cookies when a user logs into their bank account and sends it to the command-and-control server. Cookies are valuable for threat actors because they help them evade fingerprinting checks and avoid the requirement of user authentication tokens in some instances.
The malware was capable of stealing data such as passwords and account balance from official banking apps. For some apps, it was able to avoid fingerprint logins.
SharkBot seems to be targeting users in Australia, Austria, Germany, Italy, Poland, Spain, the UK, and the US.
The developers are still hard at work improving the malware and Fox-IT expects more campaigns in the future.
To avoid falling prey to such apps, don't download apps from unknown publishers, especially those that don't seem to be popular and also go through reviews.












Things that are NOT allowed: