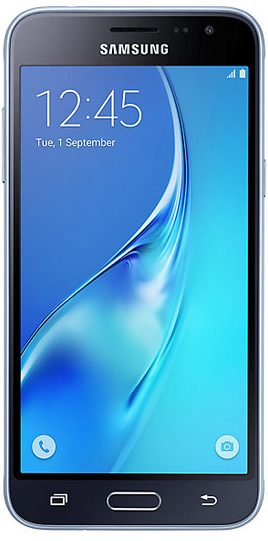
Even though the phone showed it received all updates from 2017, the Samsung J3 actually missed 12 of them
A security outfit located in German says that some Android phone manufacturers are pulling the wool over their customers' eyes. Researchers working for Security Research Labs (SRL) discovered that companies like Google, HTC, Samsung, Sony, Motorola, ZTE, TCL and others are skipping over some Android security patch updates even though the phones show that they were installed.
SRL checked out the firmware on 1,200 Android handsets and looked for every patch disseminated in 2017. The results were interesting. Outside of the
Google Pixel and
Google Pixel 2, the tests revealed that even high-end flagship models made by the top manufacturers had Android security patch updates skipped over, even if the update was credited on the phone. By showing users that these patches were installed when they weren't, owners believe that their handsets are safer than they really are.
SRL founder Karsten Nohl says that in some cases, a manufacturer might accidentally miss a security patch update, or even two. But the
Samsung J3 (2016) claimed to have every 2017 Android patch installed when in truth it had missed 12 updates, including a pair that were considered "critical" to keeping the handset safe and secure.
Besides manufacturers, SRL said some chip makers are to blame. In particular, phones powered by a MediaTek chipset had 9.7 missed patches on average. That could be due to the fact that some cheaper phones using less expensive chips are more likely to miss updates. SRL founder Nohl says, "The lesson is that if you go for a cheaper device, you end up in a less well maintained part to this ecosystem."
Google says that some of the devices in the study may not have been Android certified devices, which means that Google's standards of security would not apply to them. And some patches may have been missed, says Google, because the manufacturer removed the offending feature instead of fixing it with the patch. Google is working with SRL to delve deeper into its test results.
In Amsterdam this Friday, Nohl and fellow SRL researcher Jakob Lell will present at the Hack in the Box security conference, the results of their two-year test that revealed what they call the "patch gap."
source:
Wired
Read the latest from Alan Friedman











Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: