Not just Facebook and Google: hardcore porn and real-money gambling apps openly abused Apple's 'Enterprise' program

Last week, news broke that Facebook and Google openly abused Apple's Enterprise Certificate program to get unprecedented access to private iPhone users' data. Facebook particularly used this loophole to gain root permissions which allowed the company to mine data about anything and everything on an iPhone, including private photos and videos, and Internet traffic that the company likely used to gain a competitive advantage over its rivals.
Today, we learn that it was not just Facebook and Google: dozens and dozens of hardcore pornography and real-money gambling apps used the same loophole to circumvent the App Store and bring apps to iPhones that would never have passed Apple's own rules.
Porn apps like these continue abusing the Enterprise certificate to circumvent the App Store's rules
Apple has been openly critical about other companies' security breaches (rightly so), but has itself enforced poor control over its own Enterprise Certificate program, which has made all sorts of different violations possible. The revelations come from a continued investigation by TechCrunch.
And here is how it worked:
Apple runs an Enterprise Certificate program, which is originally designed for companies to distribute internal apps to their employees and their employees only. The policy for this program explicitly says that "You may not use, distribute or otherwise make Your Internal Use Applications available to Your Customers." Apple, however, has failed to properly enforce its own rules.
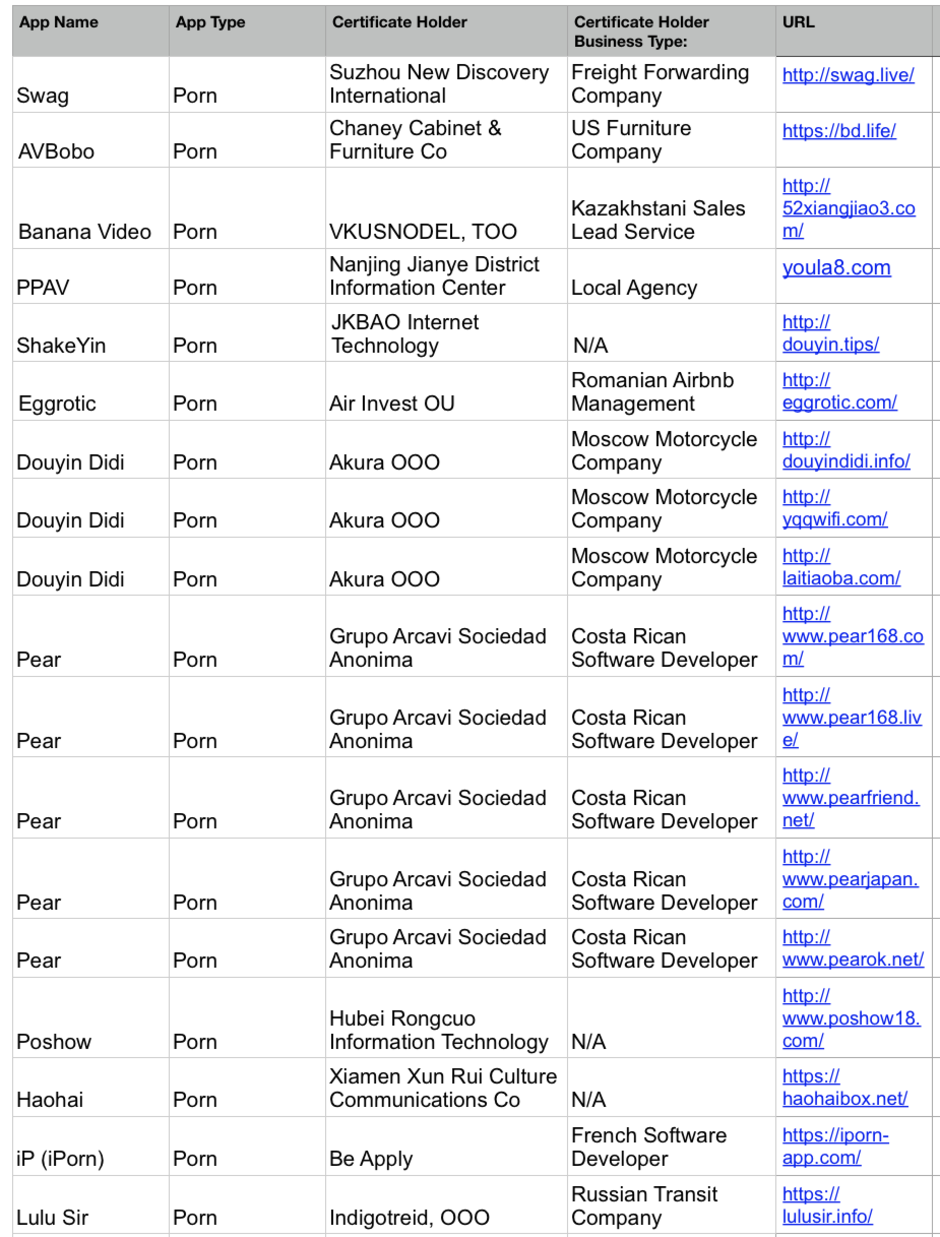
Dozens and dozens of apps misused the Enterprise program
There seem to be two ways of exploiting the Enterprise program that are used. The first one uses Apple's lax standard for accepting new business to the program. It takes filling an online form, paying a one-time $300 fee to Apple and telling a couple of lies on the phone to register a new business that could then misuse the Enterprise Certificate to distribute forbidden applications to users. The second method actually piggybacks on a legitimate certificate issued to a company. It's not clear exactly how, but developers are able to get 'rogue certificates' from a legitimate company to sign their forbidden apps and make them available to the public. Such certificate codes are then sold on various Chinese marketplaces and you could have up to a dozen of different forbidden apps piggybacking on one legitimate certificate.
Some of these apps are not explicitly malicious and do not mind user data as aggressively as Facebook did with its Facebook Research VPN app, while some 'helper tool' apps would install tracking and adware codes.

TechCrunch could easily install dozens of forbidden apps on an iPhone
Guardian Mobile Firewall security researcher Will Strafach said that all of that could have easily been prevented had there been more strict rules for registering a business under this program and proper audit. "Given the rampant abuse, it seems Apple could easily add stronger verification processes and more check-ups to the Enterprise Certificate program. Developers should have to do more to prove their apps’ connection with the Certificate holder, and Apple should regularly audit certificates to see what kind of apps they’re powering."
Follow us on Google News














Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: