Fancy Bear: Russian hackers planted Android malware to track Ukrainian artillery units
The hombrew artillery app that got infected
Cyber security company CrowdStrike is the one that claims it has traced the DNC leaks to Russian hacking groups, one of which is lovingly titled Fancy Bear, codename APT 28 (for advanced persistent threat). That same cooperative, with potential connections to the Russian military intelligence, has also used Android malware for its hacking purposes for the first time in Ukraine, says CrowdStrike.
The bears who code apparently posted links to an infected Android app on the Russian version of Facebook - vKontakte - and used it to track Ukrainian artillery units. The app has been developed by an Ukrainian officer to help process targeting data faster, and has been distributed in forums and profiles used by artillery unit commanders.
That's where Fancy Beat allegedly stepped in, infected the legit app, and collected communications, as well as tracked location of the Ukrainian artillery units as one more tool in the targeting arsenal of the separatist eastern regions. That's evidently the first time we learn that Android malware has been used for hacks directly at the frontlines. This report comes hot on the heels of another one that explains how the Russians hacked US-supplied Raven drones to monitor Ukrainian military positions, so mark another debut in this new type of cyber war.
Experts agree that the first salvos in the digital battlefield were fired when US and Israeli intelligence planted the Stuxnet virus to try and destroy the Iranian centrifuges, and every adversary had to mount up in response, so the blowback from these efforts has now cascaded all the way down to the Android phone of your average Ukrainian artillery officer. Sign of the times.
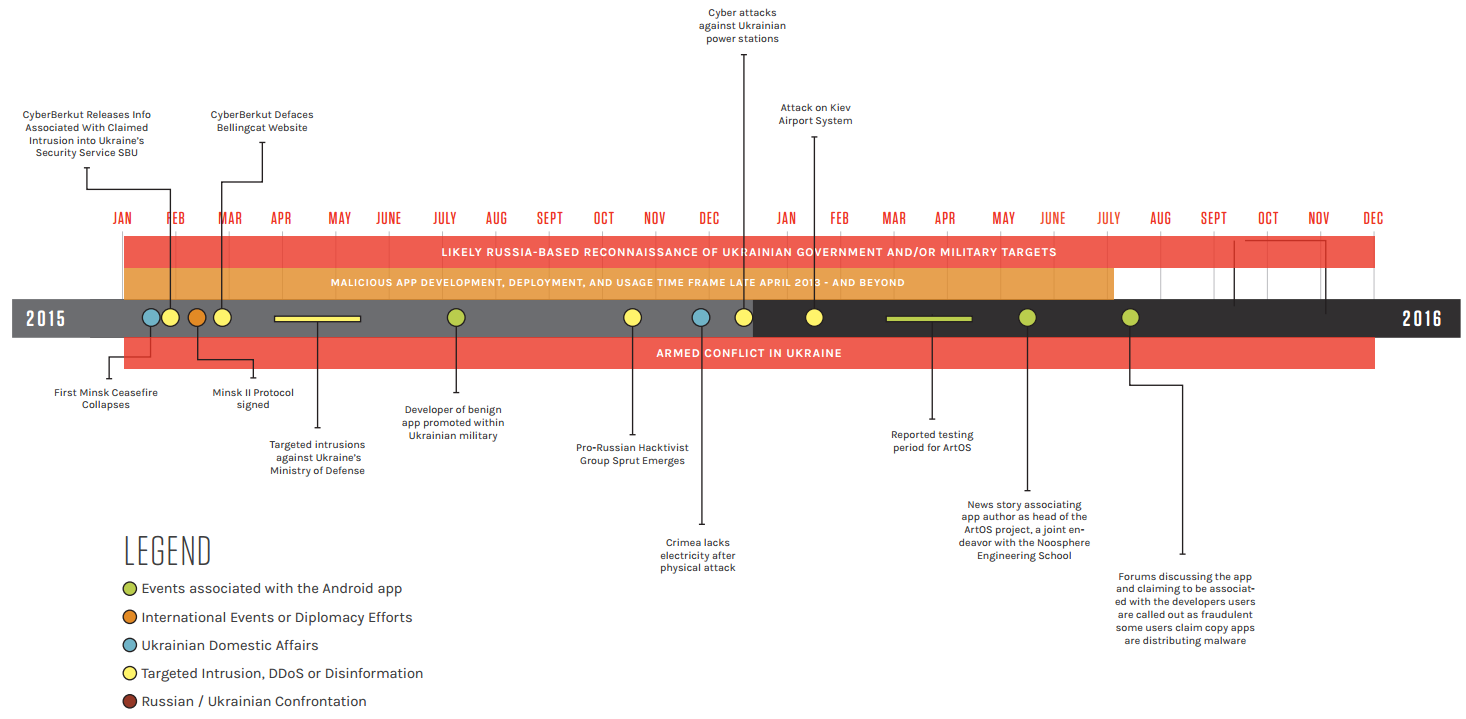
source: CrowdStrike via Reuters













Things that are NOT allowed: