Apple disputes how Google characterized the iPhone vulnerability it discovered

Toward the end of last month, we told you that Google's Project Zero team of security researchers discovered some hacked websites that were loading malware onto iOS devices. When Apple iPhone users visited these sites, even if there was no real interaction, software would be implanted inside the iPhone that would send information from the infected handset to a designated server. Practically all versions of iOS 10 through 12 were affected. Google reported the issue to Apple on February 1st of this year, and six days later iOS 12.1.4 was pushed out with a security patch.
Even though Google's security team apparently saved iPhone users from having their personal information sent to some remote server, Bloomberg reports that Apple is not pleased with Google's description of how pervasive this issue was. Google said that this was "a campaign exploiting iPhones en masse," while Apple says that fewer than a dozen websites were involved and the attack targeted the Uighur Muslims living in China. Apple also takes issue with Google's comment about the duration of the attack; the latter says that iPhone users were exposed to it for two years while Apple says that the vulnerabilities were up for "roughly two months." However, Google's Threat Analysis Group (TAG) said that it found exploits "covering almost every version from iOS 10 through to the latest version of iOS 12. This indicated a group making a sustained effort to hack the users of iPhones in certain communities over a period of at least two years."
Apple has been promoting the iPhone as a device that keeps its users' personal information private and secure
Yesterday, Google said that it stands by its in-depth research and also issued a statement. In its report, the Alphabet unit warned that while the campaign was a failure for this one attacker, "there are almost certainly others that are yet to be seen."
"[Project Zero] posts technical research that is designed to advance the understanding of security vulnerabilities, which leads to better defensive strategies. [We] will continue to work with Apple and other leading companies to help keep people safe online"-Google
As we pointed out in our original article, it is a good idea to stay away from shady websites. In this case though, it didn't matter if you interacted with the hacked site; as soon as an iPhone visited the webpage, the phone became infected. And hackers could send an email with links to these sites claiming that you've won a prize, or use other techniques to get you to click on that link, visit the suspect website and infect your iPhone.
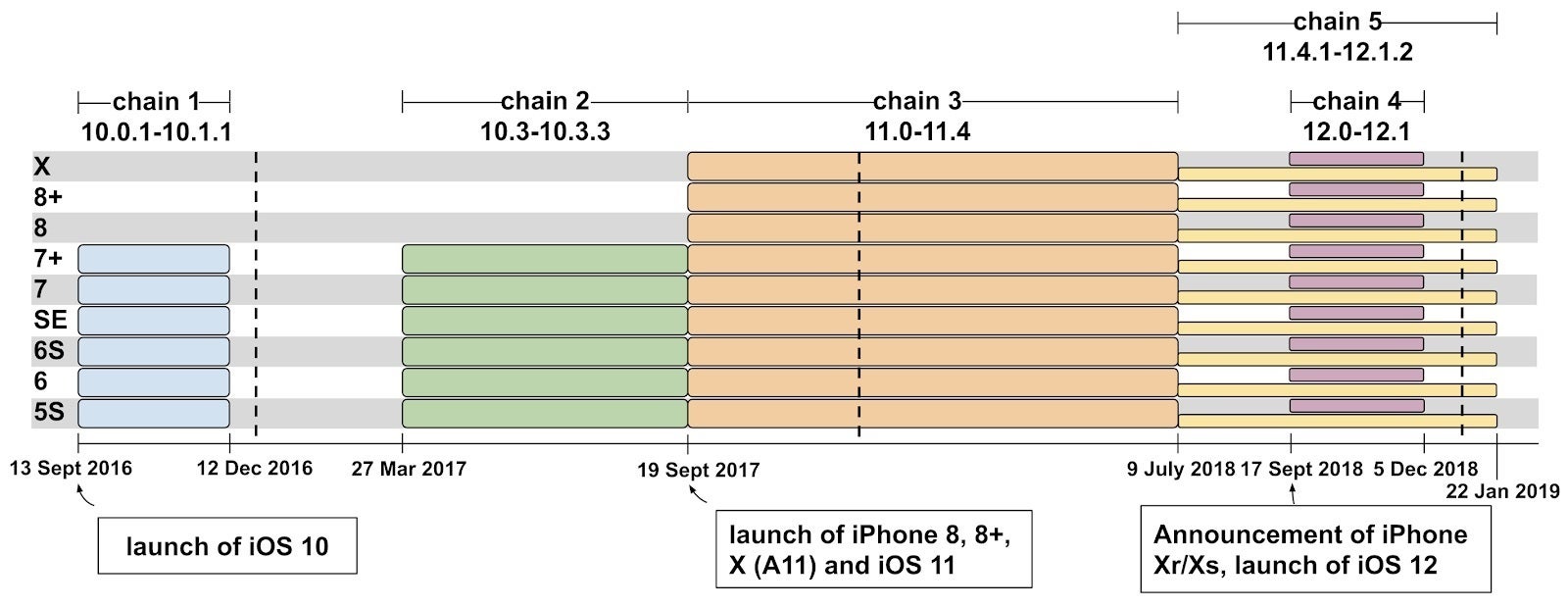
Google's Project Zero team and Threat Analysis Group found five exploit chains covering iOS 10 through iOS 12
Apple might have felt the need to have corrected Google because of its privacy campaign. You might recall that early this year during the Consumer Electronics Show (CES) in Las Vegas, Apple put up a huge billboard on the side of a hotel that overlooks the Las Vegas Convention Center, the venue that hosts the popular annual expo. The billboard was a riff on the famous "What happens in Las Vegas, stays in Las Vegas" line created by the Las Vegas Convention and Visitors Authority to attract visitors. Apple's billboard read, "What happens on your iPhone, stays on your iPhone." Apparently, there was no room on the billboard to add "...unless your iPhone visited a hacked website."

Apple promoting the security of the iPhone during the Consumer Electronics Show in Las Vegas this past January
The report from Project Zero noted that "simply visiting the hacked site was enough for the exploit server to attack your device, and if it was successful, install a monitoring implant. We estimate that these sites receive thousands of visitors per week." So while it is certainly in Apple's interest to play down this attack, it surely seems to have been as serious and widespread as Google claims it was.










Things that are NOT allowed: