Android users warned about new threat after one victim loses $280K

Cybercriminals are forever coming up with new ways to game the system. It makes you wonder if they are so smart, why didn't they do anything better with their lives? This post is not for gushing about the intelligence of online criminals of course. It's about a new Android malware called FjordPhantom.
Discovered by security company Promon, FjordPhantom is a malware using strategies never seen before. What makes it scary is that it's very good at avoiding detection.
The malware is believed to be wreaking havoc in Asian countries Indonesia, Thailand, Vietnam, Singapore, and Malaysia. One victim was swindled out of 10 million Thai Baht or around $280,000.
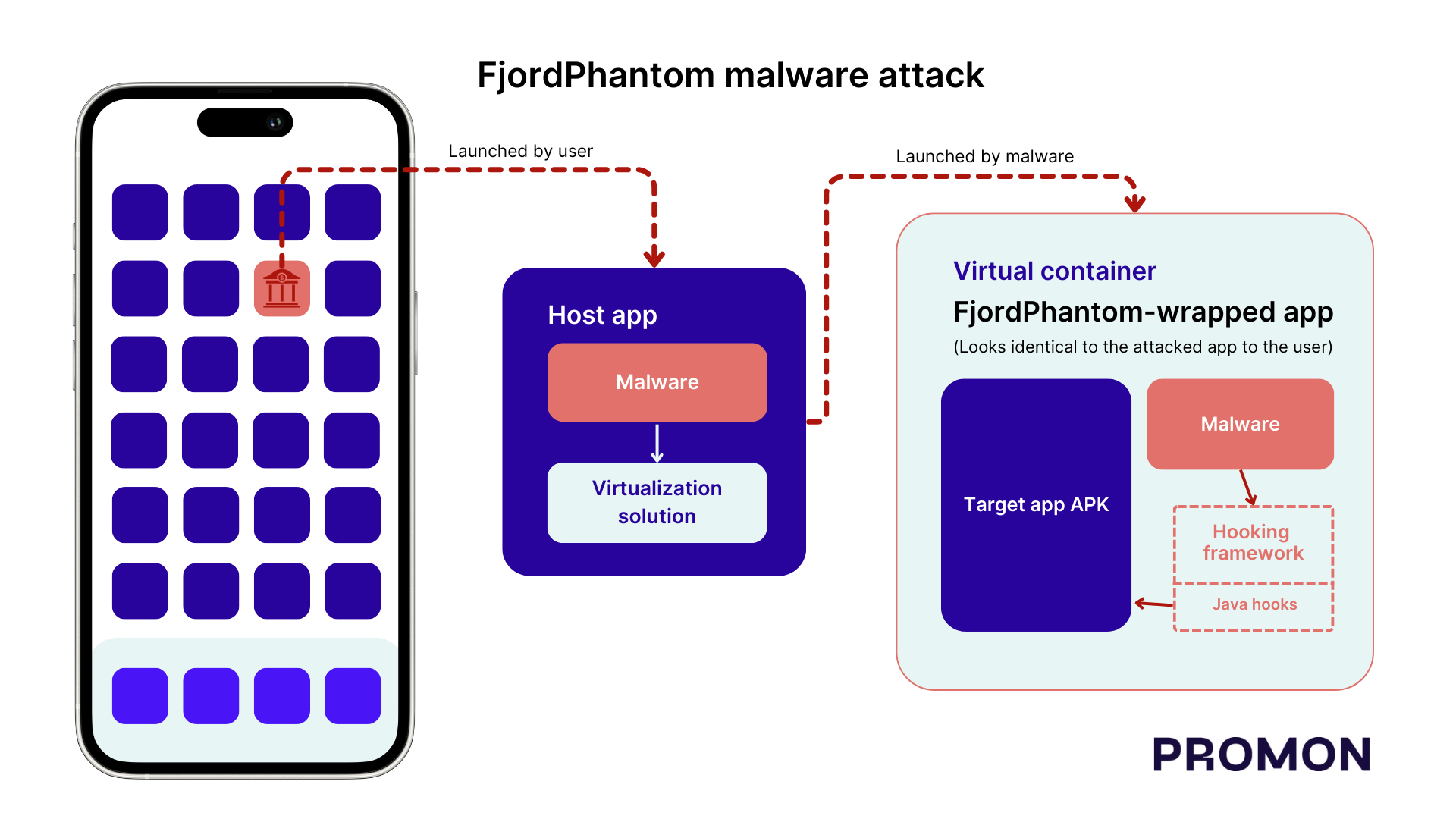
The attack is initiated by sending an email or message to a victim with a prompt to download a legitimate banking app. The catch is that once the app is downloaded, it's run in a virtual environment to give attackers control over what's happening. Virtualization provides a private execution environment for running code and helps you do things such as download the same app twice so it can be used by two users sharing the same device.
The malware also uses a hooking framework to intercept various actions. Hooking is a technique used to change how apps or operating systems behave.
There's also a social element to the attack: after an app is downloaded, the cybercriminals call the victim, posing as a customer service representative from the bank to help with running the app. This step can help the attacker trick the victim into performing a transaction or revealing credentials.
By downloading a legitimate app into a virtual filesystem and using hooking, FjordPhantom messes with how an app is normally handled by Android to flag any shady behavior.
Since the app is installed in a virtual container, it breaks the Android sandbox, which is a security feature that isolates an app's code and data from other apps and the system. This way, if one app is malicious, it cannot manipulate other apps or the core system.
Without sandboxing, apps can access each other files and inject code into each other. It also eliminates the need for root access and prevents root detection.
In short, these tactics allow FjordPhantom to carry out attacks without being detected as a user would never know it's using a virtualization solution. Using the hooking framework, it prevents the system from things such as alerting users about use of screenreaders to steal sensitive information.
Promon believes that FjordPhantom will continue to evolve. To protect yourself, make sure you only download apps from trusted sources and avoid giving out sensitive information over the phone, even if the person on the other end is claiming to be from your bank as banks typically never request its customers for such info on a phone call.
Google has reassured Android users that they don't need to panic.
Users are protected by Google Play Protect, which can warn users or block apps known to exhibit malicious behavior on Android devices with Google Play Services, even when those apps come from sources outside of Google Play." - Google Spokesperson













Things that are NOT allowed: