Replacing a screen can get your phone hacked
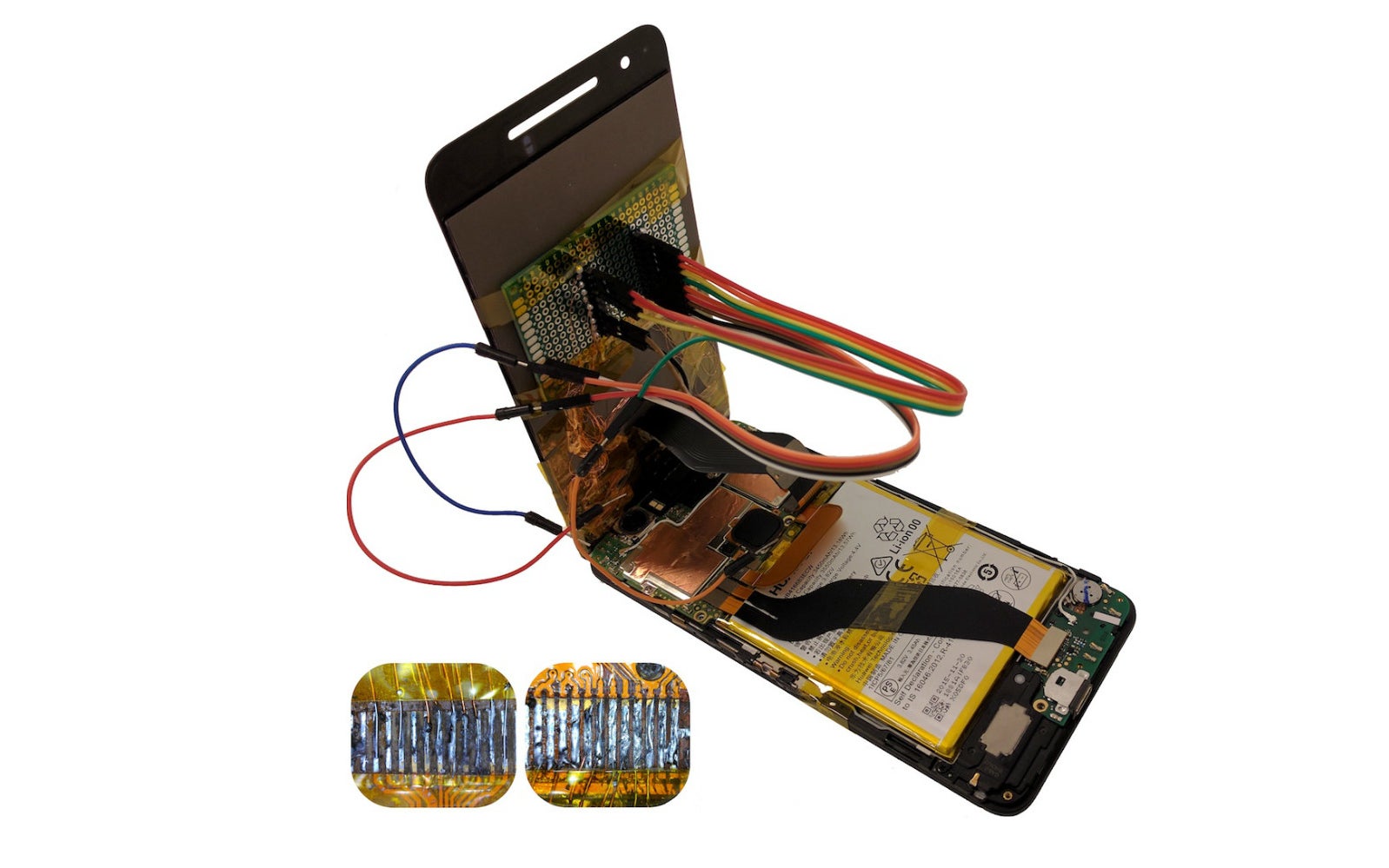
In a recently-published paper, Israeli researchers from the Ben-Gurion University of the Negev highlighted the threat of malicious peripheral existing inside consumer electronics. The team was able to booby-trap a third-party smartphone replacement screen. This was done with the help of a chip that can manipulate the data transfer from the device's hardware to the software drivers within the OS.
The code found on this chip can be used to install malicious apps, replace user-selected URLs with phishing URLs, the logging of unlock patterns and keyboard inputs, and even taking pictures of the user and forwarding them via e-mail. The nasty peripheral can even turn off the power of the screen while the above actions are performed. Furthermore, the researchers claim that this "chip-in-the-middle" attack was performed with parts that cost less than $10 which can easily be mass-produced. To put the cherry on the cake, these booby-trapped displays can apparently be made to look identical to their stock counterparts and are invisible to most detection techniques, as the process is file-less.
In the demonstration video (see below), one can see this method working on the Huawei Nexus 6P, but the researchers warn that iOS devices can be hacked just as easily. While the team also outlined several low-cost countermeasures which manufacturers can employ to combat such malicious peripherals, it is currently unknown when or if these will be implemented. As such, it would be advisable to stick to certified parts and service shops for the time being.
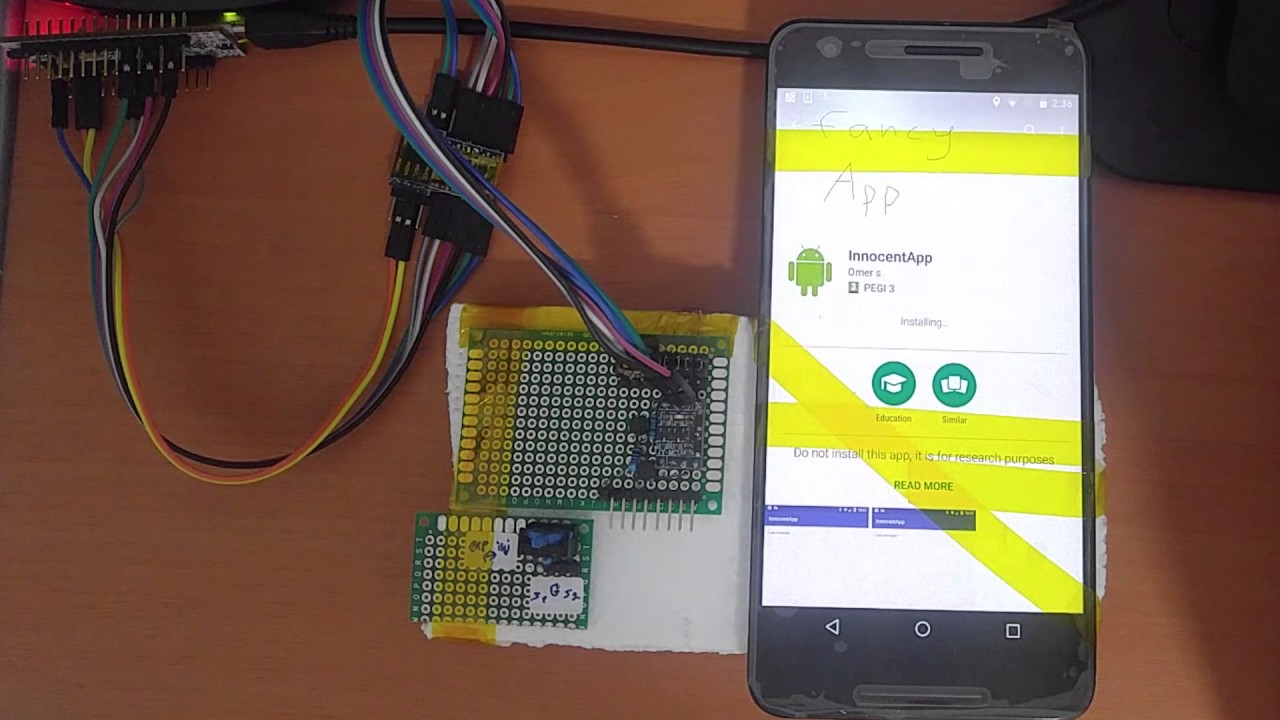
Source: Yossi Oren via Engadget
Follow us on Google News









Things that are NOT allowed:
To help keep our community safe and free from spam, we apply temporary limits to newly created accounts: